Subsections of Cybersecurity Tools and Cyberattacks
History of Cybersecurity
Today’s Cybersecurity Challenge
Threats > ⇾ Alerts > ⇾ Available Analyst < -⇾ Needed Knowledge > ⇾ Available Time <
By 2022, there will be 1.8 millions unfulfilled cybersecurity jobs.
SOC(Security Operation Center) Analyst Tasks
- Review security incidents in SIEM (security information and even management)
- Review the data that comprise the incident (events/flows)
- Pivot the data multiple ways to find outliers (such as unusual domains, IPs,
file access)
- Expand your search to capture more data around that incident
- Decide which incident to focus on next
- Identify the name of the malware
- Take these newly found IOCs (indicators of compromise) from the internet and search them back in SIEM
- Find other internal IPs which are potentially infected with the same malware
- Search Threat Feeds, Search Engine, Virus Total and your favorite tools for these outliers/indicators; Find new malware is at play
- Start another investigation around each of these IPs
- Review the payload outlying events for anything interesting (domains, MD5s, etc.)
- Search more websites for IOC information for that malware from the internet
From Ronald Reagan/War Games to where we are Today
- He was a Hollywood actor as well as US-president
- He saw a movie War Games, where a teenager hacker hacked into the Pentagon artificial intelligent computer to play a game of thermonuclear war using a dial-up connection, which was actually played using real missiles due to miss-configuration
Impact of 9/11 on Cybersecurity
- What happens if 9/11 in tech-space? Like hack and destruction of SCADA system used in dams and industrial automation systems etc.
Nice early operations
Clipper Chip: (NSA operation for tapping landline phones using some kind of chip)
↔
Moonlight Maze: (in the 2000s, process to dump passwords of Unix/Linux servers investigated by NSA/DOD affected many US institutions)
↔
Solar Sunrise: (series of attack on DOD computers on FEB 1998, exploited known vulnerability of operating system, attack two teenagers in California, one of whom was an Israeli)
↔
Buckshot Yankee: (series of compromises in year 2008, everything starts with USB inserted in Middle East military base computer, remained on the network for 14 months, Trojan used was agent.BTZ)
↔
Desert Storm: (early 90s, some radars used to alert military forces about airplanes are tampered by feeding fake information of Saddam’s regime)
↔
Bosnia: (Bosnia war, fake news to military field operations etc.)
Cybersecurity Introduction
- Every minute, thousands of tweets are sent, and millions of videos are watched.
- Due to IOT (Internet of Things) and mobile tech, we have a lot to protect.
- We have multiple vendors now, which become complicated to track for security vulnerabilities.
Things to Consider when starting a Cybersecurity Program
How and where to start?
- Security Program: Evaluate, create teams, baseline, identify and model threats, use cases, risk, monitoring, and control.
- Admin Controls: Policies, procedures, standards, user education, incident response, disaster recovery, compliance and physical security.
- Asset Management: Classifications, implementation steps, asset control, and documents.
- Tech Controls: Network infrastructure, endpoints, servers, identity management, vulnerability management, monitoring and logging.
Cybersecurity – A Security Architect’s Perspective
What is Security?
A message is considered secure when it meets the following criteria of CIA triad.
Confidentiality ↔ Authentication ↔ Integrity
Computer Security, NIST (National Institute of Standards and Technology) defined.
“The protection afforded to an automated information system in order to attain the applicable objectives to preserving the integrity, availability, and Confidentiality of information system resources. Includes hardware, software, firmware, information/data, and telecommunications.”
Additional Security Challenges
Security not as simple as it seems
- Easy requirements, tough solution
- Solutions can be attacked themselves
- Security Policy Enforcement structure can complicate solutions
- Protection of enforcement structure can complicate solutions
- Solution itself can be easy but complicated by protection
- Protectors have to be right all the time, attackers just once
- No one likes security until it’s needed, seat belt philosophy.
- Security Architecture require constant effort
- Security is viewed as in the way
What is Critical Thinking?
Beyond Technology: Critical Thinking in Cybersecurity
“The adaption of the processes and values of scientific inquiry to the special circumstances of strategic intelligence.”
- Cybersecurity is a diverse, multi faced field
- Constantly changing environment
- Fast-paced
- Multiple stakeholders
- Adversary presence
- Critical thinking forces you to think and act in situations where there are no clear answers nor specific procedures.
- Part Art, Part Science: This is subjective and impossible to measure.
Critical Thinking: A Model
- Hundreds of tools updating always with different working models, so critical thinking is more important than ever to approach problems in more pragmatic way.
- Interpersonal skills for working with other people and sharing information.
Critical Thinking – 5 Key Skills
-
1) Challenge Assumption
Explicitly list all Assumptions ↔ Examine each with key Q’s ↔ Categorize based on evidence ↔ refine and remove ↔ Identify additional data needs
-
2) Consider alternatives
Brainstorm ↔ The 6 W’s (who/what/when/where/why/how) ↔ Null hypothesis
-
3) Evaluate data
- Know your DATA
- Establish a baseline for what’s normal
- be on the lookout for inconsistent data
- proactive
-
4) Identify key drivers
- Technology
- Regulatory
- Society
- Supply Chain
- Employee
- Threat Actors
-
5) Understand context
Operational environment you’re working in. Put yourself in other’s shoe, reframe the issue.
- Key components
- Factors at play
- Relationships
- similarities/differences
- redefine
A Brief Overview of Types of Threat Actors and their Motives
- Internal Users
- Hackers (Paid or not)
- Hacktivism
- Governments
Motivation Factors
- Just to play
- Political action and movements
- Gain money
- Hire me! (To demonstrate what can I do for somebody to hire me or use my services)
Hacking organizations
- Fancy Bears (US election hack)
- Syrian Electronic Army
- Guardians of the peace (Leaked Sony Data about film regarding Kim Jong-un to prevent its release)
Nation States
- NSA
- Tailored Access Operations (USA)
- GCHQ (UK)
- Unit 61398 (China)
- Unit 8200 (Israel)
Major different types of cyberattacks
- Sony Hack
Play-station Hack by a Hacktivist group called Lutz (2011).
- Singapore cyberattack
Anonymous attacked multiple websites in Singapore as a protest (2013).
- Multiple Attacks
E-bay, Home-Depot, UBISOFT, LinkedIn, Gobiemos
- Target Hack
More than 100 million of credit cards were leaked (2015).
Malware and attacks
- SeaDaddy and SeaDuke (CyberBears US Election)
- BlackEnergy 3.0 (Russian Hackers)
- Shamoon (Iran Hackers)
- Duqu and Flame (Olympic Games US and Israel)
- DarkSeoul (Lazarous and North Korea)
- WannaCry (Lazarous and North Korea)
An Architect’s perspective on attack classifications
Security Attack Definition
Two main classifications
-
Passive attacks
- Essentially an eavesdropping styles of attacks
- Second class is traffic analysis
- Hard to detect the passive nature of attack as just traffic is monitored not tampered
-
Active Attacks
- Explicit interception and modification
- Several classes of these attack exist
Examples
- Masquerade (Intercepting packets as someone else)
- Replay
- Modification
- DDoS
Security Services
“A process or communication service that is provided by a system, to give a specific kind of protection to a system resource.”
- Security services implement security policies. And are implemented by security mechanisms
X.800 definition:
“a service provided by a protocol layer of communicating open systems, which ensures adequate security of the systems or of data transfers”
RFC 2828:
“a processing or communication service provided by a system to give a specific kind of protection to system resources”
Security Service Purpose
- Enhance security of data processing systems and information transfers of an organization
- Intended to counter security attacks
- Using one or more security mechanisms
- Often replicates functions normally associated with physical documents
- which, for example, have signatures, dates; need protection from disclosure, tampering, or destruction, be notarized or witnessed; be recorded or licensed
Security Services, X.800 style
- Authentication
- Access control
- Data confidentiality
- Data integrity
- Non-repudiation (protection against denial by one of the parties in a communication)
- Availability
Security Mechanisms
- Combination of hardware, software, and processes
- That implement a specific security policy
- Protocol suppression, ID and Authentication, for example
- Mechanisms use security services to enforce security policy
- Specific security mechanisms:
- Cryptography, digital signatures, access controls, data integrity, authentication exchange, traffic padding, routing control, notarization
- Pervasive security mechanisms
- Trusted functionality, security labels, event detection, security audit trails, security recovery
Network Security Model
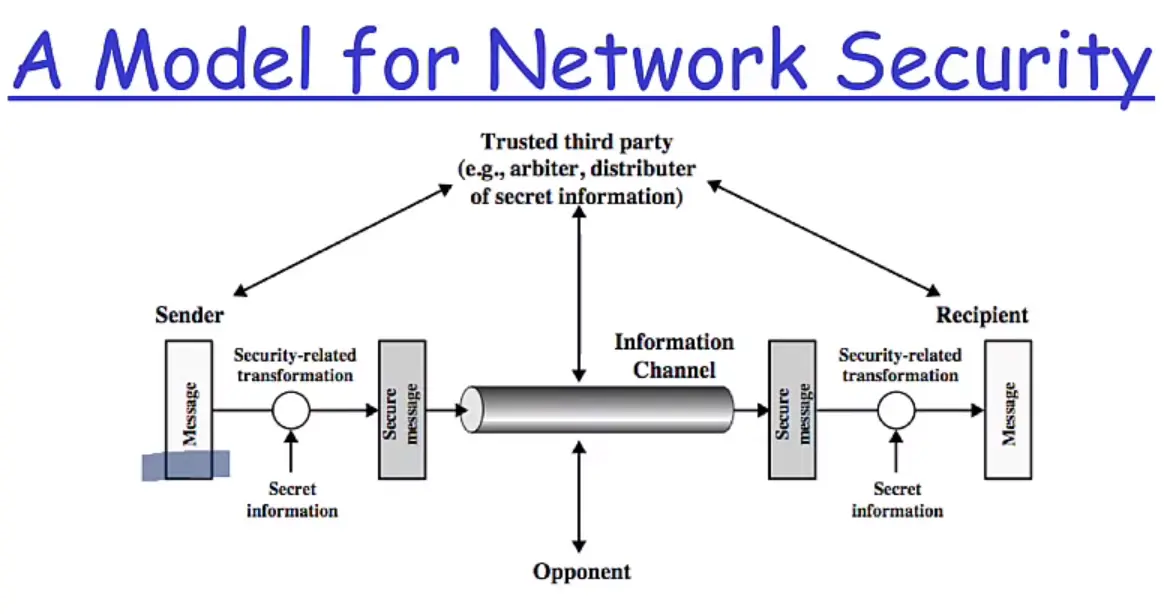

Security Architecture is Context
According to X.800:
- Security: It is used in the sense of minimizing the vulnerabilities of assets and resources.
- An asset is anything of value
- A vulnerability is any weakness that could be exploited to violate a system or the information it contains
- A threat is a potential violation of security
Security Architecture and Motivation
The motivation for security in open systems
- a) Society’s increasing dependence on computers that are accessed by, or linked by, data communications and which require protection against various threats;
- b) The appearance in several countries of “data protection” which obliges suppliers to demonstrate system integrity and privacy;
- c) The wish of various organizations to use OSI recommendations, enhanced as needed, for existing and future secure systems
Security Architecture – Protection
What is to be protected?
- a) Information or data;
- b) communication and data processing services; and
- c) equipment and facilities
Organizational Threats
The threats to a data communication system include the following
- a) destruction of information and/or other resources
- b) corruption or modification of information
- c) theft, removal, or loss of information and/or other resources
- d) disclosure of information; and
- e) interruption of services
Types of Threats
- Accidental threats do not involve malicious intent
- Intentional threats require a human with intent to violate security.
- If an intentional threat results in action, it becomes an attack.
- Passive threats do not involve any (non-trivial) change to a system.
- Active threats involve some significant change to a system.
Attacks
“An attack is an action by a human with intent to violate security.”
- It doesn’t matter if the attack succeeds. It is still considered an attack even if it fails.
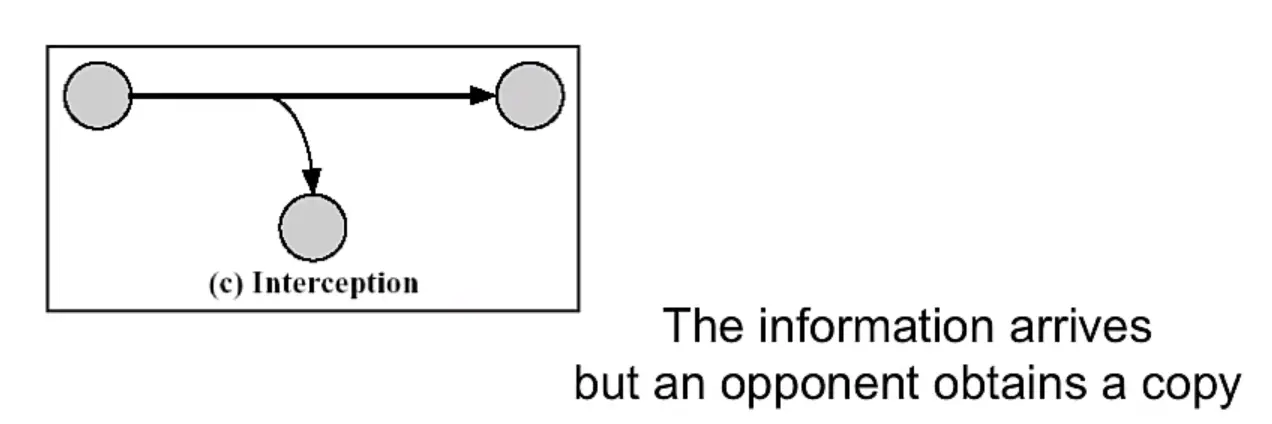
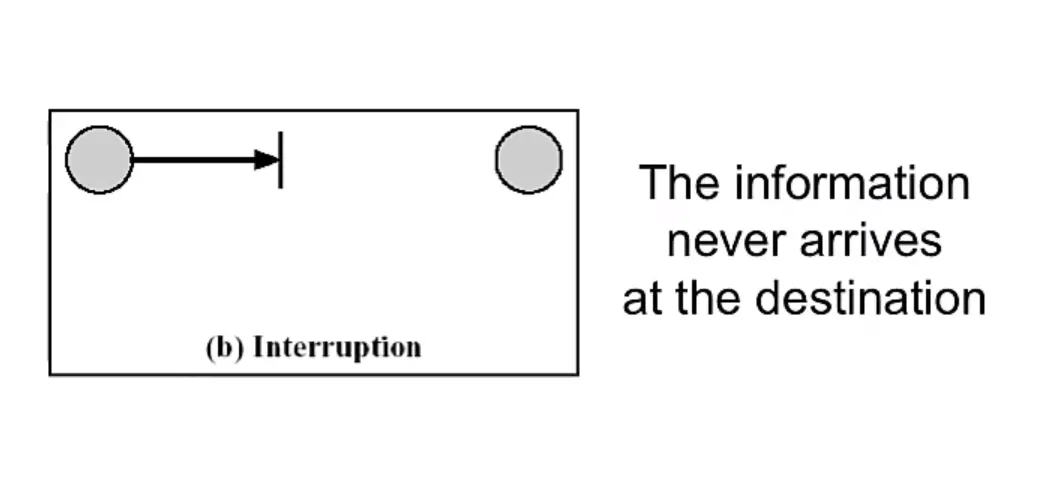
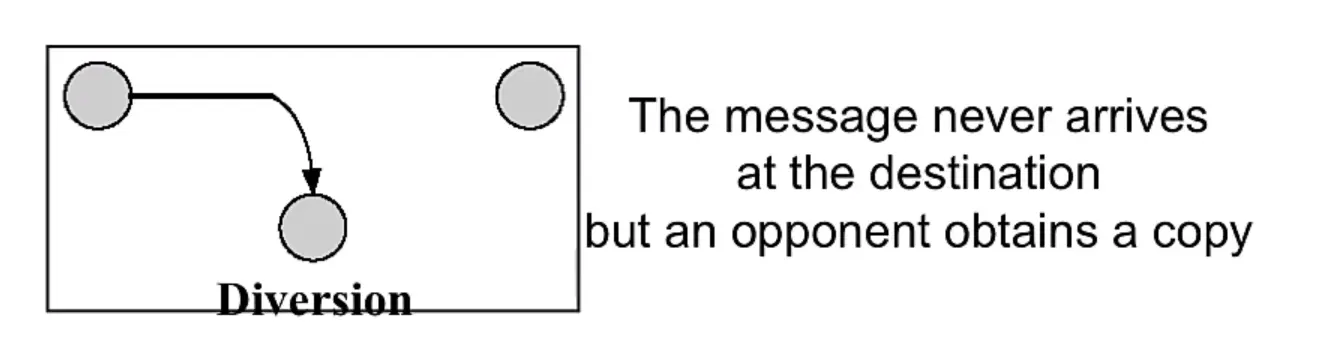
Passive Attacks
Two more forms:
- Disclosure (release of message content)
This attacks on the confidentiality of a message.
- Traffic analysis (or traffic flow analysis)
also attacks the confidentiality
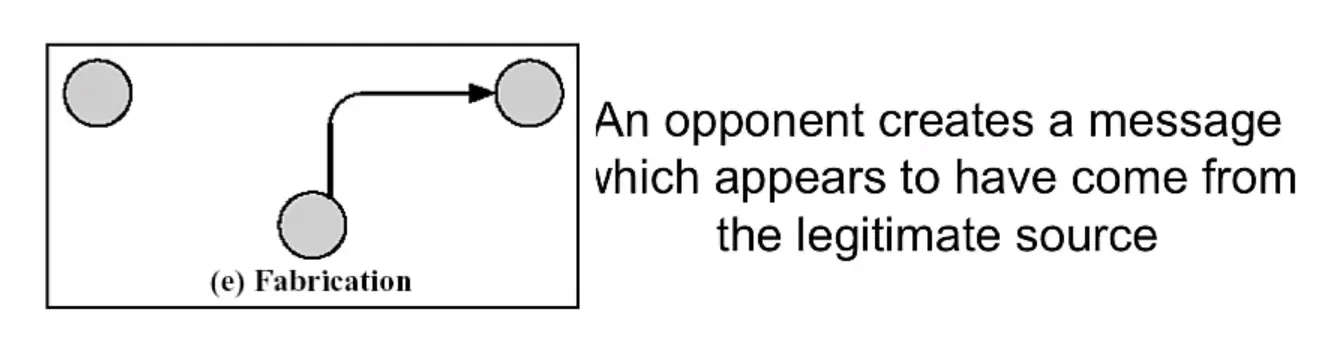
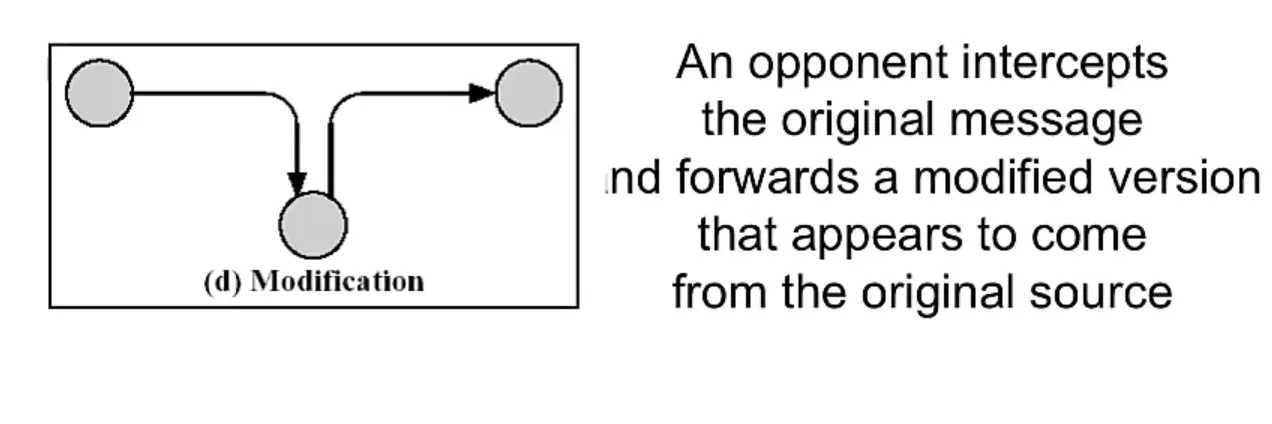
Active Attacks
Fours forms:
- I) Masquerade: impersonification of a known or authorized system or person
- II)Replay: a copy of a legitimate message is captured by an intruder and re-transmitted
- III) Modification
- IV) Denial of Service: The opponent prevents authorized users from accessing a system.
Security Architecture – Attacks models
Passive Attacks

Active Attacks




Malware and an Introduction to Threat Protection
Malware and Ransomware
- Malware: Short for malicious software, is any software used to disrupt computer or mobile operations, gather sensitive information, gain access to private computer systems, or display unwanted advertising. Before the term malware was coined by Yisrael Radai in 1990. Malicious software was referred to as computer viruses.
Types of Malware
- Viruses
- Worms
- Trojans Horses
- Spyware
- Adware
- RATs
- Rootkit
- Ransomware: A type of code which restricts the user’s access to the system resources and files.
Other Attack Vectors
- Botnets
- Keyloggers
- Logic Bombs (triggered when certain condition is met, to cripple the system in different ways)
- APTs (Advanced Persistent Threats: main goal is to get access and monitor the network to steal information)
Some Known Threat Actors
- Fancy Bears: Russia
- Lazarous Groups: North Korea
- Periscope Group: China
Threat Protection
- Technical Control
- Antivirus (AV)
- IDS (Intrusion Detection System)
- IPS (Intrusion Protection System)
- UTM (Unified Threat Management)
- Software Updates
- Administrative Control
- Policies
- Trainings (social engineering awareness training etc.)
- Revision and tracking (The steps mentioned should remain up-to-date)
Additional Attack Vectors Today
Internet Security Threats – Mapping
Mapping
- before attacking; “case the joint" – find out what services are implemented on network
- Use ping to determine what hosts have addresses on network
- Post scanning: try to establish TCP connection to each port in sequence (see what happens)
- NMap Mapper: network exploration and security auditing
Mapping: Countermeasures
- record traffic entering the network
- look for suspicious activity (IP addresses, ports being scanned sequentially)
- use a host scanner and keep a good inventory of hosts on the network
- Red lights and sirens should go off when an unexpected ‘computer’ appears on the network
Internet Security Threats – Packet Sniffing
Packet Sniffing
- broadcast media
- promiscuous NIC reads all packets passing by
- can read all unencrypted data
Packet Sniffing – Countermeasures
- All hosts in the organization run software that checks periodically if host interface in promiscuous mode.
- One host per segment of broadcast media.
Internet Security Threats – IP Spoofing
IP Spoofing
- can generate ‘raw’ IP packets directly from application, putting any value into IP source address field
- receiver can’t tell if source is spoofed
IP Spoofing: ingress filtering
- Routers should not forward out-going packets with invalid source addresses (e.g., data-gram source address not in router’s network)
- Great, but ingress can not be mandated for all networks
Internet Security Threats – Denial of Service
Denial of service
- flood of maliciously generated packets ‘swamp’ receiver
- Distributed DOS: multiple coordinated sources swamp receiver
Denial of service – Countermeasures
- filter out flooded (e.g., SYN) before reaching host: throw out good with bad
- trace-back to source of floods (most likely an innocent, compromised machine)
Internet Security Threats – Host insertions
Host insertions
- generally an insider threat, a computer ‘host’ with malicious intent is inserted in sleeper mode on the network
Host insertions – Countermeasures
- Maintain an accurate inventory of computer hosts by MAC addresses
- Use a host scanning capability to match discoverable hosts again known inventory
- Missing hosts are OK
- New hosts are not OK (red lights and sirens)
Attacks and Cyber Crime Resources
The Cyber Kill Chain
- Reconnaissance: Research, identification and selection of targets
- Weaponizations: Pairing remote access malware with exploit into a deliverable payload (e.g., adobe PDF and Microsoft Office files)
- Delivery: Transmission of weapon to target (e.g., via email attachments, websites, or USB sticks)
- Exploitation: Once delivered, the weapon’s code is triggered, exploiting vulnerable application or systems
- Installation: The weapon installs a backdoor on a target’s system allowing persistent access
- Command & Control: Outside server communicates with the weapons providing ‘hands on keyboard access’ inside the target’s network.
- Actions on Objectives: the attacker works to achieve the objective of the intrusion, which can include ex-filtration or destruction of data, or intrusion of another target.
What is Social Engineering?
“The use of humans for cyber purposes”
- Tool: The Social-Engineer Toolkit (SET)
Phishing
“To send fake emails, URLs or HTML etc.”
Vishing
“Social Engineering via Voice and Text.”
Cyber warfare
- Nation Actors
- Hacktivist
- Cyber Criminals
An Overview of Key Security Concepts
CIA Triad
CIA Triad – Confidentiality
“To prevent any disclosure of data without prior authorization by the owner.”
- We can force Confidentiality with encryption
- Elements such as authentication, access controls, physical security and permissions are normally used to enforce Confidentiality.
CIA Triad – Integrity
- Normally implemented to verify and validate if the information that we sent or received has not been modified by an unauthorized person of the system.
- We can implement technical controls such as algorithms or hashes (MD5, SHA1, etc.)
CIA Triad – Availability
- The basic principle of this term is to be sure that the information and data is always available when needed.
- Technical Implementations
- RAIDs
- Clusters (Different set of servers working as one)
- ISP Redundancy
- Back-Ups
Non-Repudiation – How does it apply to CIA?
“Valid proof of the identity of the data sender or receiver”
- Technical Implementations:
Access Management
- Access criteria
- Groups
- Time frame and specific dates
- Physical location
- Transaction type
- “Needed to Know” Just access information needed for the role
- Single Sign-on (SSO)
Incident Response
“Computer security incident management involves the monitoring and detection of security events on a computer or a computer network and the execution of proper resources to those events. Means the information security or the incident management team will regularly check and monitor the security events occurring on a computer or in our network.”
Incident Management
- Events
- Incident
- Response team: Computer Security Incident Response Team (CSIRT)
- Investigation
Key Concepts – Incident Response
E-Discovery
Data inventory, helps to understand the current tech status, data classification, data management, we could use automated systems. Understand how you control data retention and backup.
Automated Systems
Using SIEM, SOA, UBA, Big data analysis, honeypots/honey-tokens. Artificial Intelligence or other technologies, we could enhance the mechanism to detect and control incidents that could compromise the tech environment.
BCP (Business Continuity Plan) & Disaster Recovery
Understand the company in order to prepare the BCP. A BIA, it’s good to have a clear understanding of the critical business areas. Also indicate if a security incident will trigger the BCP or the Disaster Recovery.
Post Incident
Root-Cause analysis, understand the difference between error, problem and isolated incident. Lessons learned and reports are a key.
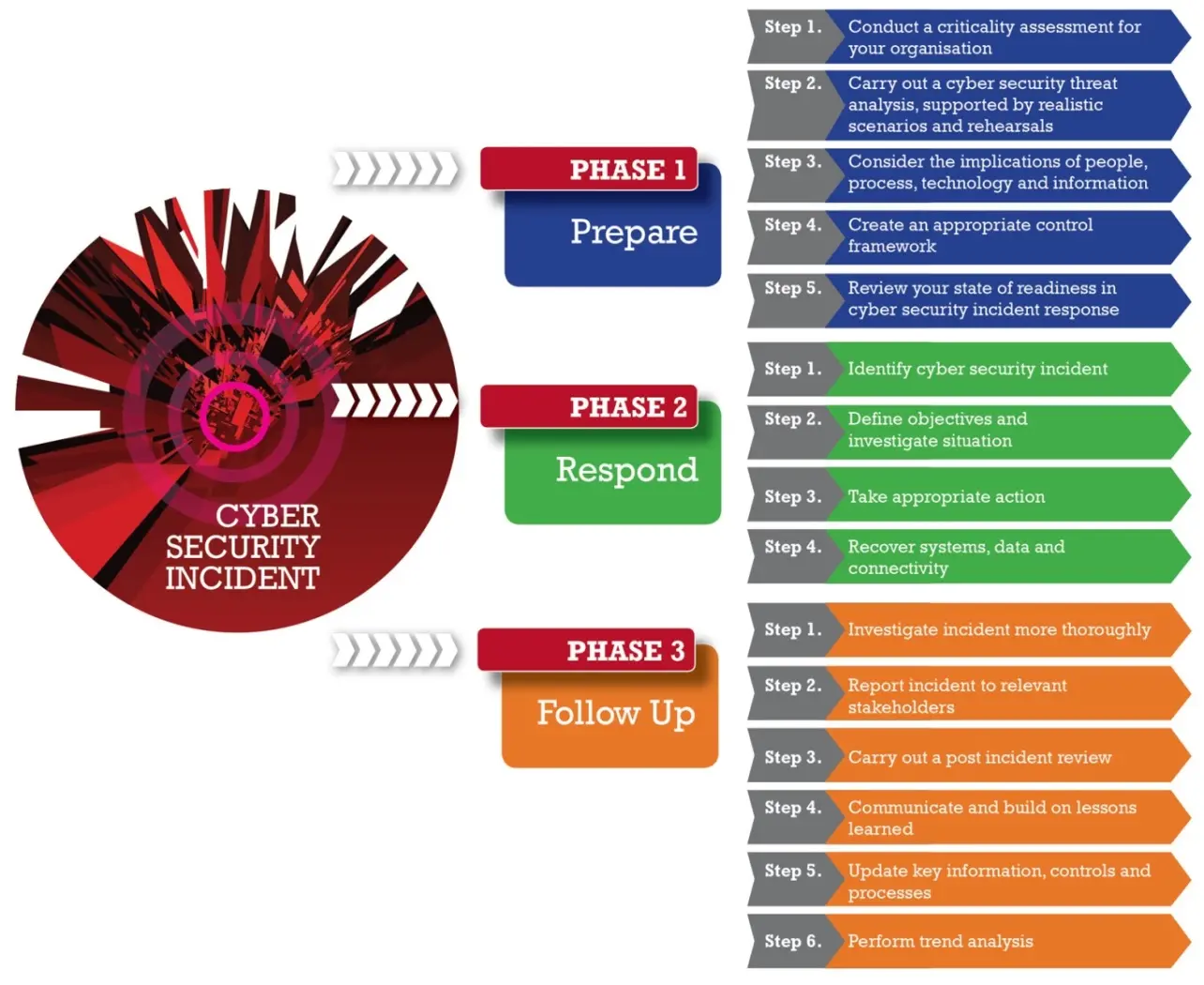
Incident Response Process
- Prepare
- Respond
- Follow up

Introduction to Frameworks and Best Practices
Best Practices, baseline, and frameworks
- Used to improve the controls, methodologies, and governance for the IT departments or the global behavior of the organization.
- Seeks to improve performance, controls, and metrics.
- Helps to translate the business needs into technical or operational needs.
Normative and compliance
- Rules to follow for a specific industry.
- Enforcement for the government, industry, or clients.
- Event if the company or the organization do not want to implement those controls, for compliance.
Best practices, frameworks, and others
- COBIT
- ITIL
- ISOs
- COSO
- Project manager methodologies
- Industry best practices
- Developer recommendations
- others
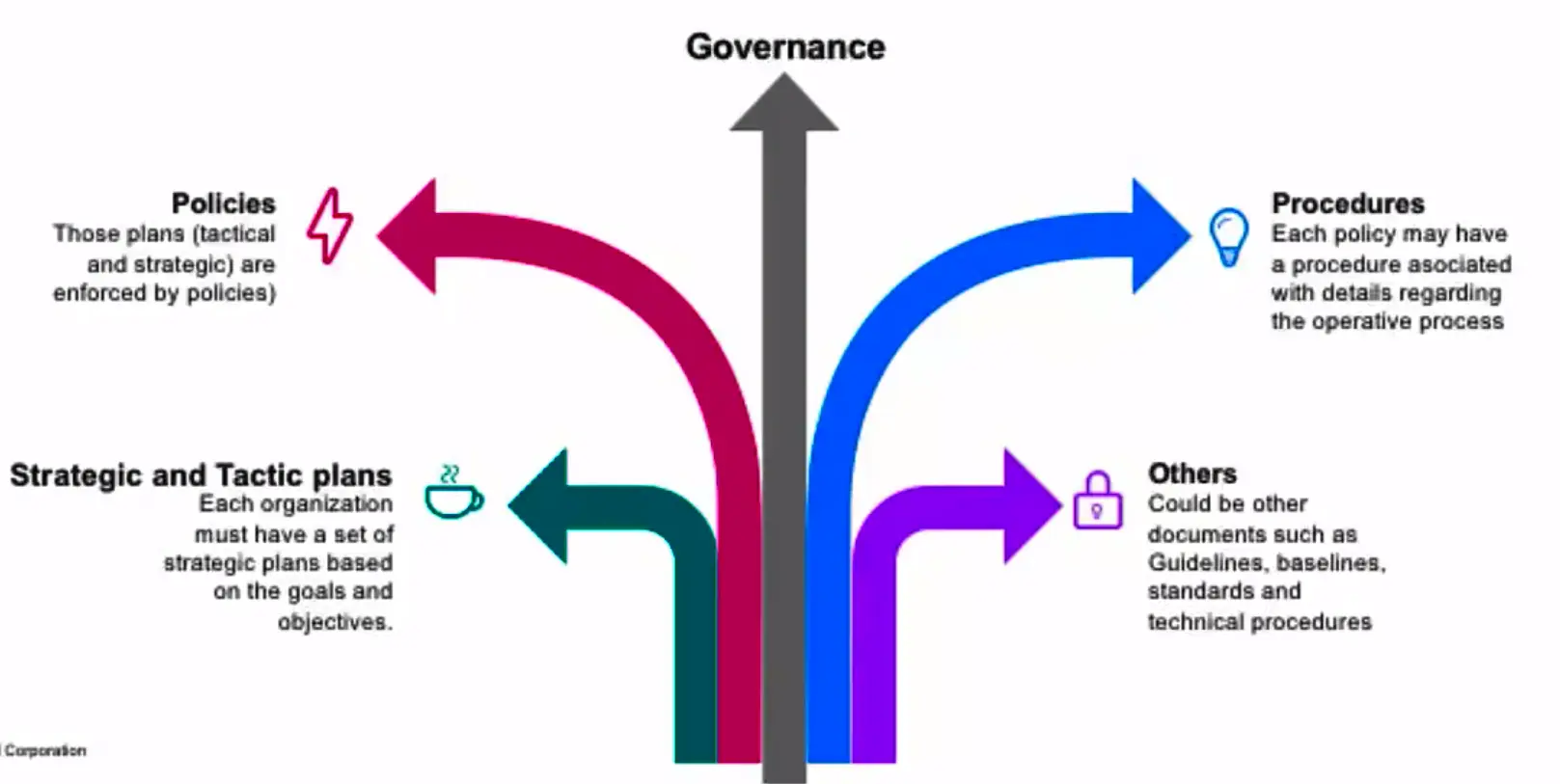
IT Governance Process
Security Policies, procedures, and other
- Strategic and Tactic plans
- Procedures
- Policies
- Governance
- Others

Cybersecurity Compliance and Audit Overview
Compliance;
- Audit
- Define audit scope and limitations
- Look for information, gathering information
- Do the audit (different methods)
- Feedback based on the findings
- Deliver a report
- Discuss the results
Pentest Process and Mile 2 CPTE Training
Pentest – Ethical Hacking
A method of evaluating computer and network security by simulating an attack on a computer system or network from external and internal threats.
Introduction to Firewalls
Firewalls
“Isolates the organization’s internal net from the larger Internet, allowing some packets to pass, while blocking the others.”
Firewalls – Why?
- Prevent denial-of-service attacks;
- SYN flooding: attacker establishes many bogus TCP connections, no resources left for “real” connections.
- Prevent illegal modification/access of internal data.
- e.g., attacker replaces CIA’s homepage with something else.
- Allow only authorized access to inside network (set of authenticated users/hosts)
- Two types of Firewalls
- Application level
- Packet filtering
Firewalls – Packet Filtering
- Internal network connected to internet via router firewall
- router filters packet-by-packet, decision to forward/drop packet based on;
- source IP address, destination IP address
- TCP/UDP source and destination port numbers
- ICMP message type
- TCP SYNC and ACK bits
Firewalls – Application Gateway
- Filters packets on application data as well as on IP/TCP/UDP fields.
- Allow select internal users to telnet outside:
- Require all telnet users to telnet through gateway.
- For authorized users, the gateway sets up a telnet connection to the destination host. The gateway relays data between 2 connections.
- Router filter blocks all telnet connections not originating from gateway.
Limitations of firewalls and gateways
- IP spoofing: router can’t know if data “really” comes from a claimed source.
- If multiple app’s need special treatment, each has the own app gateway.
- Client software must know how to contact gateway.
- e.g., must set IP address of proxy in Web Browser.
- Filters often use all or nothing for UDP.
- Trade-off: Degree of communication with outside world, level of security
- Many highly protected sites still suffer from attacks.
Firewalls – XML Gateway
- XML traffic passes through a conventional firewall without inspection;
- All across normal ‘web’ ports
- An XML gateway examines the payload of the XML message;
- Well formed (meaning to specific) payload
- No executable code
- Target IP address makes sense
- Source IP is known
Firewalls – Stateless and Stateful
Stateless Firewalls
- No concept of “state”.
- Also called Packet Filter.
- Filter packets based on layer 3 and layer 4 information (IP and port).
- Lack of state makes it less secure.
Stateful Firewalls
- Have state tables that allow the firewall to compare current packets with previous packets.
- Could be slower than packet filters but far more secure.
- Application Firewalls can make decisions based on Layer 7 information.
Proxy Firewalls
- Acts as an intermediary server.
- Proxies terminate connections and initiate new ones, like a MITM.
- There are two 3-way handshakes between two devices.
Antivirus/Anti-malware
- Specialized software that can detect, prevent and even destroy a computer virus or malware.
- Uses malware definitions.
- Scans the system and search for matches against the malware definitions.
- These definitions get constantly updated by vendors.
An Introduction of Cryptography
- Cryptography is secret writing.
- Secure communication that may be understood by the intended recipient only.
- There is data in motion and data at rest. Both need to be secured.
- Not new, it has been used for thousands of years.
- Egyptians hieroglyphics, Spartan Scytale, Caesar Cipher, are examples of ancient Cryptography.
Cryptography – Key Concepts
- Confidentiality
- Integrity
- Authentication
- Non-repudiation
- Crypto-analysis
- Cipher
- Plaintext
- Ciphertext
- Encryption
- Decryption
Cryptographic Strength
- Relies on math, not secrecy.
- Ciphers that have stood the test of time are public algorithms.
- Mono-alphabetic < Poly-alphabetic Ciphers
- Modern ciphers use Modular math
- Exclusive OR(XOR) is the “secret sauce” behind modern encryption.
Types of Cipher
- Stream Cipher: Encrypt or decrypt, a bit per bit.
- Block Cipher: Encrypt or decrypt in blocks or several sizes, depending on the algorithms.
Types of Cryptography
Three main types;
- Symmetric Encryption
- Asymmetric Encryption
- Hash
Symmetric Encryption
- Use the same key to encrypt and decrypt.
- Security depends on keeping the key secret at all times.
- Strengths include speed and Cryptographic strength per a bit of key.
- The bigger the key, the stronger the algorithm.
- Key need to be shared using a secure, out-of-band method.
- DES, Triples DES, AES are examples of Symmetric Encryption.
Asymmetric Encryption
- Whitefield Diffie and Martin Hellman, who created the Diffie-Hellman. Pioneers of Asymmetric Encryption.
- Uses two keys.
- One key ban be made public, called public key. The other one needs to be kept private, called Private Key.
- One for encryption and one for decryption.
- Used in digital certificates.
- Public Key Infrastructure – PKI
- It uses “one-way” algorithms to generate the two keys. Like factoring prime numbers and discrete logarithm.
- Slower than Symmetric Encryption.
Hash Functions
- A hash function provides encryption using an algorithm and no key.
- A variable-length plaintext is “hashed” into a fixed-length hash value, often called a “message digest” or simply a “hash”.
- If the hash of a plaintext changes, the plaintext itself has changed.
- This provides integrity verification.
- SHA-1, MD5, older algorithms prone to collisions.
- SHA-2 is the newer and recommended alternative.
Cryptographic Attacks
- Brute force
- Rainbow tables
- Social Engineering
- Known Plaintext
- Known ciphertext
DES: Data Encryption Standard
- US encryption Standard (NIST, 1993)
- 56-bit Symmetric key, 64-bit plaintext input
- How secure is DES?
- DES Challenge: 56-bit-key-encrypted phrase (“Strong Cryptography makes the world a safer place”) decrypted (brute-force) in 4 months
- No known “back-doors” decryption approach.
- Making DES more secure
- Use three keys sequentially (3-DES) on each datum.
- Use cipher-block chaining.
AES: Advanced Encryption Standard
- New (Nov. 2001) symmetric-key NIST standard, replacing DES.
- Processes data in 128-bit blocks.
- 128, 192, or 256-bit keys.
- Brute-force decryption (try each key) taking 1 sec on DES, takes 149 trillion years for AES.
First look at Penetration Testing and Digital Forensics
Penetration Testing – Introduction
- Also called Pentest, pen testing, ethical hacking.
- The practice of testing a computer system, network, or application to find security vulnerabilities that an attacker could exploit.
Hackers
- White Hat
- Grey Hat
- Black Hat
Threat Actors
“An entity that is partially or wholly responsible for an incident that affects or potentially affects an organization’s security. Also referred to as malicious actor.”
- There are different types;
- Script kiddies
- Hacktivists
- Organized Crime
- Insiders
- Competitors
- Nation State
- Fancy Bear (APT28)
- Lazarous Group
- Scarcruft (Group 123)
- APT29
Pen-test Methodologies


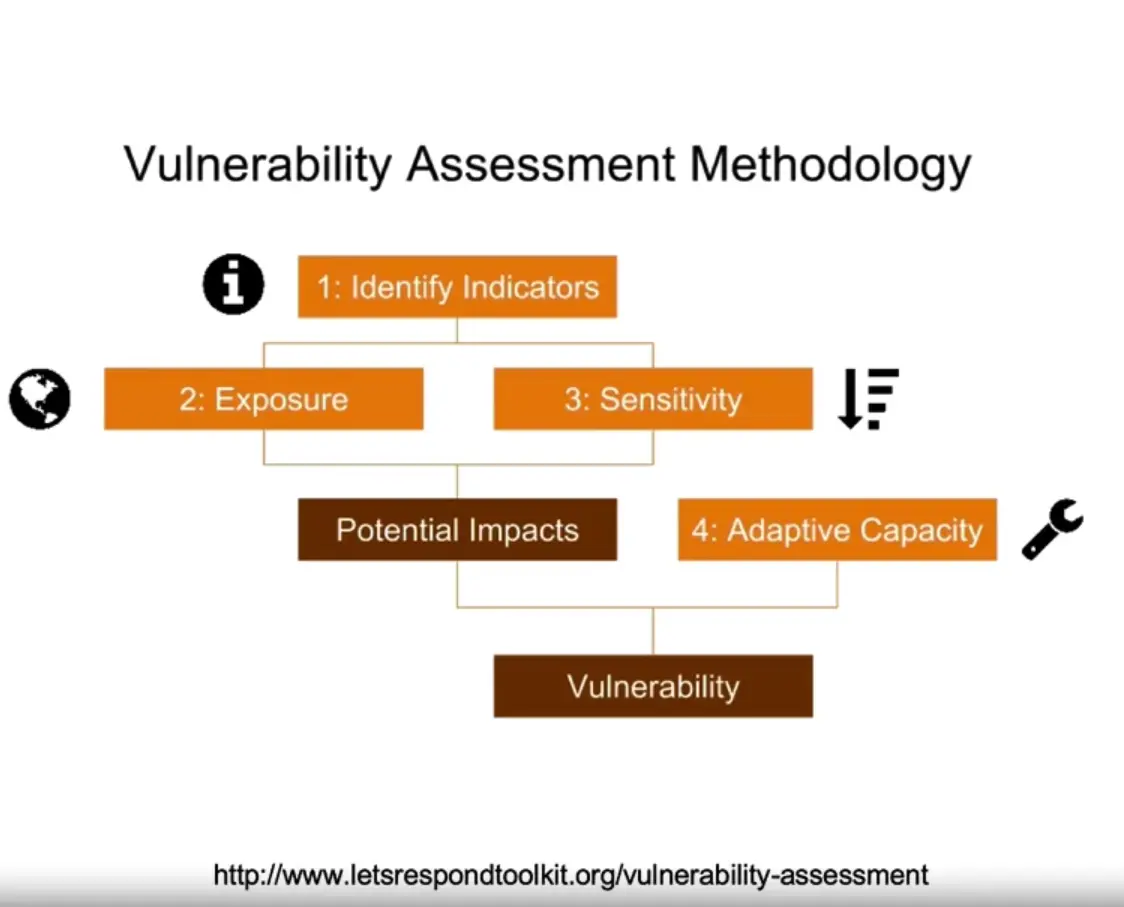
Vulnerability Tests

What is Digital Forensics?
- Branch of Forensics science.
- Includes the identification, recovery, investigation, validation, and presentation of facts regarding digital evidence found on the computers or similar digital storage media devices.
Locard’s Exchange Principle
DR. Edmond Locard;
“A pioneer in Forensics science who became known as the Sherlock Holmes of France.”
- The perpetrator of a crime will bring something into the crime scene and leave with something from it, and that both can be used as Forensic evidence.
Chain of Custody
- Refers to the chronological documentation or paper trail that records the sequence of custody, control, transfer, analysis, and disposition of physical or electronic evidence.
- It is often a process that has been required for evidence to be shown legally in court.
- Hardware
- Faraday cage
- Forensic laptops and power supplies, tool sets, digital camera, case folder, blank forms, evidence collection and packaging supplies, empty hard drives, hardware write blockers.
- Software
VolatilityFTK (Paid)EnCase (Paid)ddAutopsy (The Sleuth Kit)Bulk Extractor, and many more.