Network Security and Database Vulnerabilities
It has following modules…
It has following modules…
Stateless means that each packet is inspected one at a time with no knowledge of the previous packets.
A stateful inspection means that each packet is inspected with knowledge of all the packets that have been sent or received from the same session.
A session consists of all the packets exchanged between parties during an exchange.
An Intrusion Detection System (IDS) is a network security technology originally built for detecting vulnerability exploits against a target application or computer.
An IPS is a network security/threat prevention technology that examines network traffic flows to detect and prevent vulnerability exploits.
Method of remapping one IP address space into another by modifying network address information in Internet Protocol (IP) datagram packet headers, while they are in transit across a traffic routing device.
Gives you an additional layer of security.
Allows the IP network of an organization to appear from the outside to use a different IP address space than what it is actually using. Thus, NAT allows an organization with non-globally routable addresses to connect to the Internet by translating those addresses into a globally routable addresses space.
It has become a popular and essential tool in conserving global address space allocations in face of IPv4 address exhaustion by sharing one Internet-routable IP address of a NAT gateway for an entire private network.
Layer 3 or network layer adds an address to the data as it flows down the stack; then layer 2 or the data link layer adds another address to the data.
For a LAN to function, we need:
Connectivity between devices
A set of rules controlling the communication
The most common set of rules is called Ethernet.
To send a packet from one host to another host within the same network, we need to know the MAC address, as well as the IP address of the destination device.
Destination Layer 2 address: MAC address of the device that will receive the frame.
Source Layer 2 address: MAC address of the device sending the frame.
Types: Indicates the layer 3 protocol that is being transported on the frame such as IPv4, IPv6, Apple Tall, etc.
Data: Contains original data as well as the headers added during the encapsulation process.
Checksum: This contains a Cyclic Redundancy Check to check if there are errors on the data.
A MAC address is a 48-bits address that uniquely identifies a device’s NIC. The first 3 bytes are for the OUI and the last 3 bytes are reserved to identify each NIC.
Preamble and delimiter (SFD) are 7 byte fields in an Ethernet frame. Preamble informs the receiving system that a frame is starting and enables synchronization, while SFD (Start Frame Delimiter) signifies that the Destination MAC address field begin with the next byte.
Regenerates electrical signals.
Connects 2 or more separate physical cables.
Physical layer device.
Repeater has no mechanism to check for collision.
Ethernet bridges have 3 main functions:
VLANs provide a way to separate LANs on the same switch.
Devices in one VLAN don’t receive broadcast from devices that are on another VLAN.
The process of using layer 3 addresses to determine layer 2 addresses is called ARP or Address Resolution Protocol.
IPv4 is a 32 bits address divided into four octets.
From 0.0.0.0 to 255.255.255.255
IPv4 has 4,294,967,296 possible addresses in its address space.
When the Internet’s address structure was originally defined, every unicast IP address had a network portion, to identify the network on which the interface using the IP address was to be found, and a host portion, used to identify the particular host on the network given in the network portion.
The partitioning of the address space involved five classes. Each class represented a different trade-off in the number of bits of a 32-bit IPv4 address devoted to the network numbers vs. the number of bits devoted to the host number.
In each IPv4 subnet, a special address is reserved to be the subnet broadcast address. The subnet broadcast address is formed by setting the network/subnet portion of an IPv4 address to the appropriate value and all the bits in the Host portion to 1.
In IPv6, addresses are 128 bits in length, four times larger than IPv4 addresses.
An IPv6 address will no longer use four octets. The IPv6 address is divided into eight hexadecimal values (16 bits each) that are separated by a colon(:) as shown in the following examples: 65b3:b834:54a3:0000:0000:534e:0234:5332 The IPv6 address isn’t case-sensitive, and you don’t need to specify leading zeros in the address. Also, you can use a double colon(::) instead of a group of consecutive zeros when writing out the address.
0:0:0:0:0:0:0:1
::1
Developed by Tim Berners-Lee.
HTTP works on a request response cycle; where the client returns a response.
It is made of 3 blocks known as the start-line header and body.
Not secure.
Domain Name System or DNS translates domains names into IP addresses.
Syslog is standard for message logging. It allows separation of the software that generates messages, the system that stores them, and the software that report and analyze them. Each message is labeled with a facility code, indicating the software type generating the message, and assigned a severity label.
Used for:
System management
Security auditing
General informational analysis, and debugging messages
Used to convey event notification messages. Provides a message format that allows vendor specific extensions to be provided in a structured way.
The facility value indicates which machine process created the message. The Syslog protocol was originally written on BSD Unix, so Facilities reflect the names of the UNIX processes and daemons.
If you’re receiving messages from a UNIX system, consider using the User Facility as your first choice. Local0 through Local7 aren’t used by UNIX and are traditionally used by networking equipment. Cisco routers, for examples, use Local6 or Local7.
In computer networking, promiscuous mode (often shortened to “promisc mode” or “promisc. mode”) is a mode for a wired network interface controller (NIC) or wireless network interface controller (WNIC) that causes the controller o pass all traffic it receives to the Central Processing Unit (CPU) rather than passing only frames that the controller is intended to receive.
Traditional firewalls don’t have the fine-grained intelligence to distinguish one kind of Web traffic from another, and enforce business policies, so it’s either all or nothing.
The firewall itself must be able to monitor traffic from layers 2 through 7 and make a determination as to what type of traffic is being sent and received.
Cisco Systems have announced plans to add new levels of application visibility into its Adaptive Security Appliance (ASA), as part of its new SecureX security architecture.
Says it was the first vendor to deliver NGFW and the first to replace port-based traffic classification with application awareness. The company’s products are based on a classification engine known as App-ID. App-ID identifies applications using several techniques, including decryption, detection, decoding, signatures, and heuristics.
They use a suite of software products, known as AppSecure, to deliver NGFW capabilities to its SRX Services Gateway. The application-aware component, known as AppTrack, provides visibility into the network based on Juniper’s signature database as well as custom application signatures created by enterprise administrators.
It is a free and powerful open source firewall used mainly for FreeBSD servers. It is based on stateful packet filtering. Furthermore, it has a wide range of features that are normally only found in very expensive firewalls.
It is a powerful firewall that provides us the tools we need to run a network, and also gives us the option to scale up as and when required. It is a modular operating system that runs in a virtual environment or on some dedicated hardware in the home, office etc.
It is open source and completely free, and based on Debian GNU/Linux. It can run on both physical and virtual platforms. Not only that, but it provides a firewall, VPN functionality and software based network routing. Likewise, it also supports paravirtual drivers and integration packages for virtual platforms. Unlike OpenWRT or pfSense, VyOS provides support for advanced routing features such as dynamic routing protocols and command line interfaces.
It is an open source Linux Firewall which is secure, user-friendly, stable and easily configurable. It provides an easily understandable Web Interface to manage the firewall. Likewise, it is most suitable for small businesses and local PCs.
Network security/threat prevention technology.
Examines network traffic flows to detect and prevent vulnerability exploits.
Often sits directly behind the firewall.
It is based on a dictionary of uniquely identifiable patterns (or signatures) in the code of each exploit. As an exploit is discovered, its signature is recorded and stored in a continuously growing dictionary of signatures. Signatures detection for IPS breaks down into two types:
To create a highly available system, three characteristics should be present:
Redundancy:
Means that there are multiple components that can perform the same task. This eliminates the single point of failure problem by allowing a second server to take over a task if the first one goes down or becomes disabled.
Monitoring and Failover
In a highly available setup, the system needs to be able to monitor itself for failure. This means that there are regular checks to ensure that all components are working properly. Failover is the process by which a secondary component becomes primary when monitoring reveals that a primary component has failed.
It is a solution commonly employed to solve the network availability and performance challenges and has the ability to operate multiple NICs as a single interface from the perspective of the system.
NIC teaming provides:
“Structured data is data that has been organized into a formatted repository, typically a database, so that its elements can be made addressable for more effective processing and analysis.”
“Semi-structured data is data that has not been organized into a specialized repository, such as a database, but that nevertheless has associated information, such as metadata, that makes it more amenable to processing than raw data.”
“Unstructured data is information, in many forms, that doesn’t hew to conventional data models and thus typically isn’t a good fit for a mainstream relational database.”
Flat-file databases take all the information from all the records and store everything in one table.
Relational databases separate a mass of information into numerous tables. All columns in each table should be about one topic, such as “student information”, “class Information”, or “trainer information”.
The tables for a relational database are linked to each other through the use of Keys. Each table may have one primary key and any number of foreign keys. A foreign key is simply a primary key from one table that has been placed in another table.
The most important rules for designing relational databases are called Normal Forms. When databases are designed properly, huge amounts of information can be kept under control. This lets you query the database (search for information section) and quickly get the answer you need.
Enforce:
DOD STIG
CIS (Center for Internet Security)
CVE (Common Vulnerability and Exposures)
Secure:
Privileges
Configuration settings
Security patches
Password policies
OS level file permission
Established Baseline: User defined queries for custom tests to meet baseline for;
Organization
Industry
Application
Ownership and access for your files
Forensics: Advanced Forensics and Analytics using custom reports
Understand your sensitive data risk and exposure
Perhaps the most common day-to-day use case for a database is using it as the backend of an application, such as your organization HR system, or even your organization’s email system!
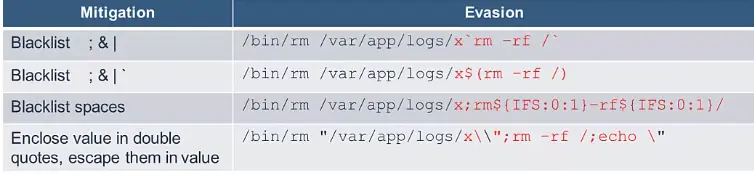
/bin/sh -c "/bin/rm /var/app/logs/../../lib/libc.so.6"/bin/sh -c "/bin/rm /var/app/logs/x;rm -rf /"rm use java.nio.file.Files.deleteIfExists(file)cp use java.nio.file.Files.copy(source, destination) … and so on.rm -rf /) he can do much less damage when the application is running as tomcat user vs. running as root user.sh, bash, cmd.exe, powershell.exe it is much easier to inject commands.rm:
/bin/sh -c "/bin/rm /var/app/logs/x;rm -rf /"/bin/rm /var/app/logs/x;rm -rf/nmap the part on the right, when injected, could overwrite a vital system file):
/usr/bin/nmap 1.2.3.4 -oX /lib/libc.so.6processfile.sh "x;rm -rf /"/usr/bin/nmap 123.45.67.89DLL hijacking.ipAddress):
Runtime.getRuntime().exec("/user/bin/nmap " + ipAddress) ;Runtime.getRuntime().exec(new String[]{"/usr/bin/nmap",ipAddress});action=delete&file=457realName= getRealFileName(fileID);
Runtime.getRuntime().exec(newString[]{"/bin/rm","/var/app/logs/"+realName});rm /var/app/logs/file

[A-Za-z0-9.]+Abuse of vulnerable application functionality that causes execution of attacker-specified SQL queries.
It is possible in any SQL database.
Made possible by lack of sufficient input sanitization.
Example
COPY (SELECT 1) TO PROGRAM 'rm -rf /'DROP TABLE sales) – injected statements may sometimes be chained
SELECT * FROM users WHERE user='' ;DROP TABLE sales; --' AND pass=''SELECT name, text FROM log WHERE data='2018-04-01' UNION SELECT user, password FROM users --'a:
IF(password LIKE 'a%', sleep(10), 'false')stmt.executeQuery("SELECT * FROM users WHERE user='"+user+"' AND pass='"pass+"'")PreparedStatement ps = conn.preparedStatement("SELECT * FROM users WHERE user = ? AND pass = ?"); ps.setString(1, user);ps.setString(2, pass);conn.preparedStatement("SELECT * FROM users WHERE user = ? AND pass = ? ORDER BY "+column);ERROR: If you have an error in your SQL syntax, check the manual that corresponds to your MySQL server version for the right syntax to use near
“x” GROUP BY username ORDER BY username ASC’ at line 1.
Query hqlQuery = session.createQuery("SELECT * FROM users WHERE user='"+user+"'AND pass='"+pass+"'")$where query parameter is interpreted as JavaScript.$where: "$expression"$where: "this.userType==3"$where: "d = new Date; do {c = new Date;} while (c - d < 100000;""//Employee[UserName/text()='" + Request ("Username") + "' AND Password/text() = '" + Request ("Password") + "']"//Employee[UserName/text()='bob' AND Password/text()='secret']//Employee[UserName/text()='' or 1=1 or '1'='1' And Password/text()='']find("(&(cn=" + user +")(password=" + pass +"))")find("(&(cn=bob)(password=secret))")find("(&(cn=*)(cn=*))(|cn=*)(password=any)")