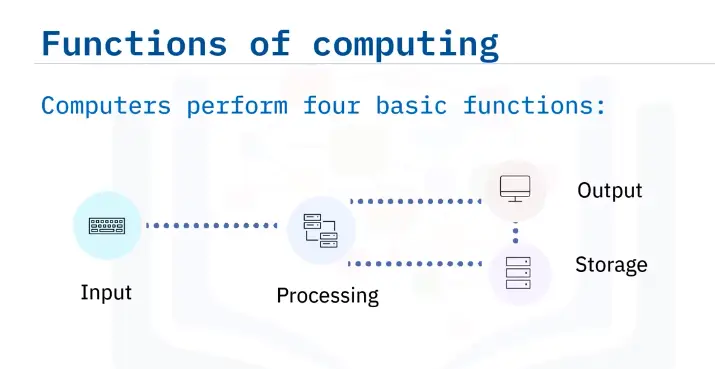
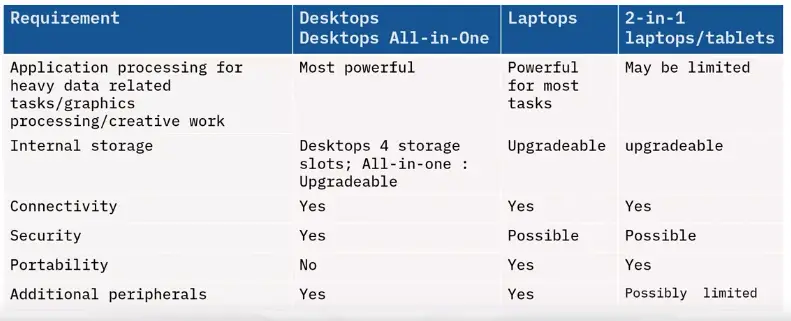
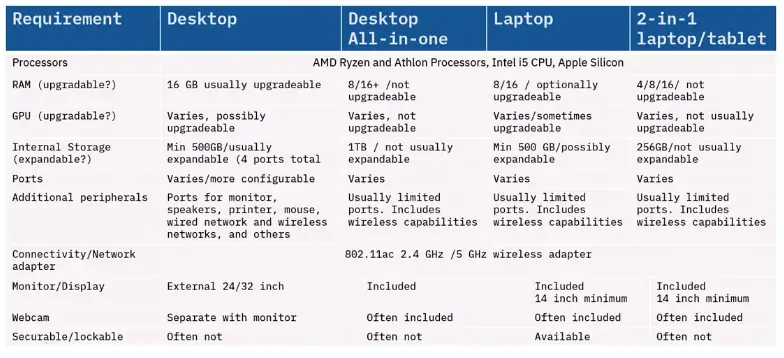
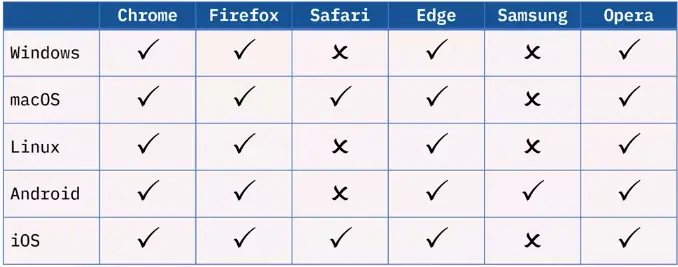
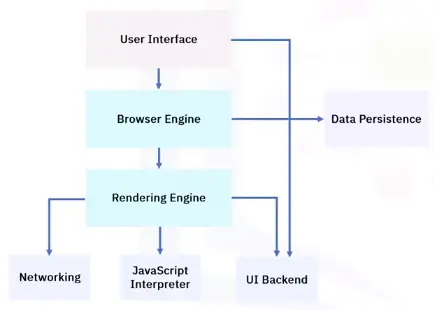
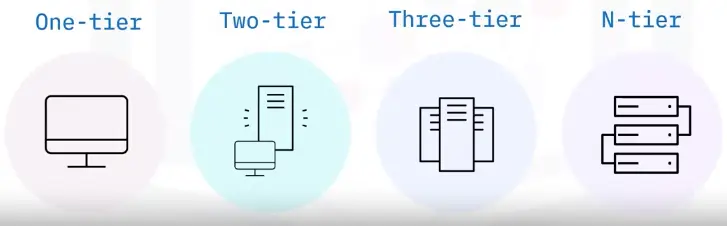
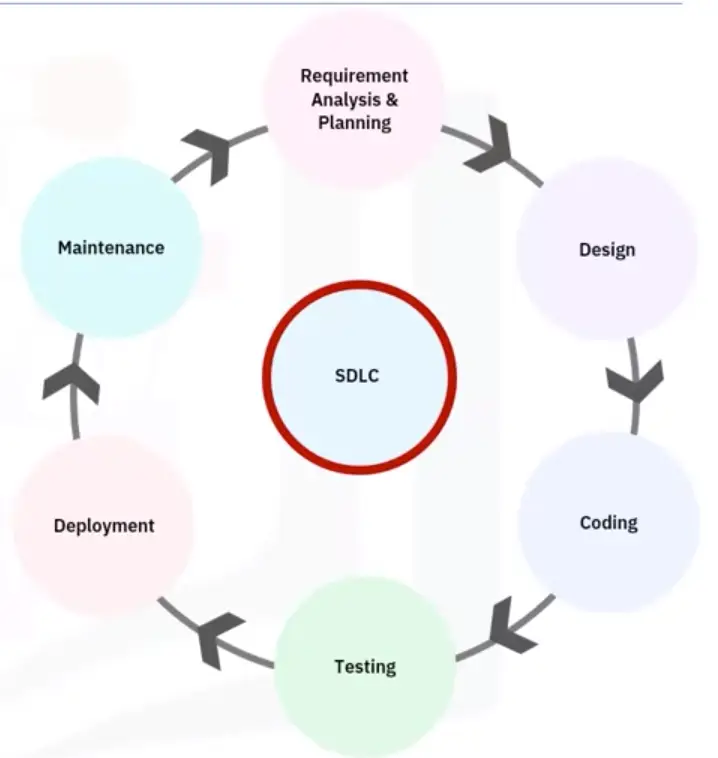
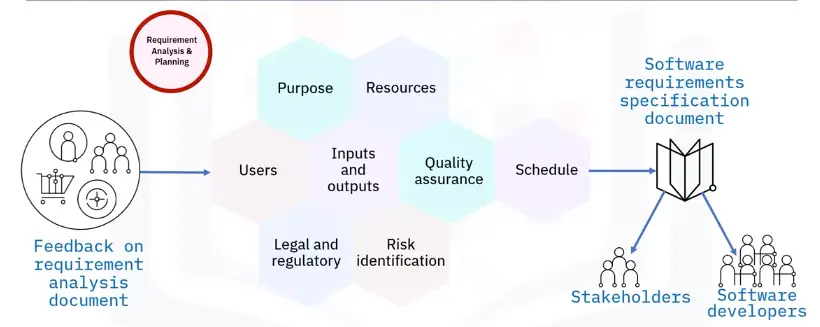
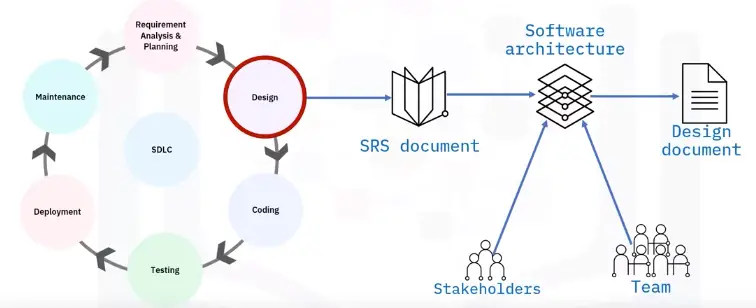
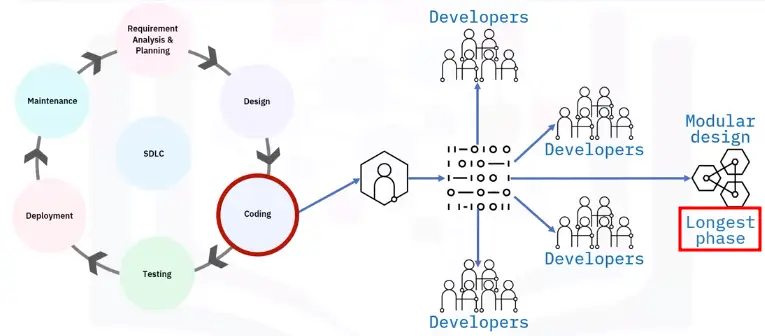
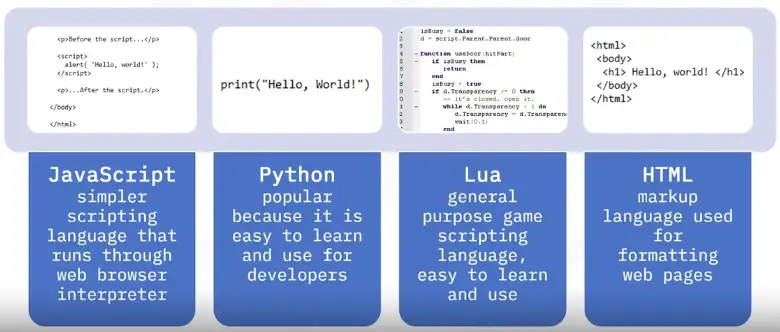
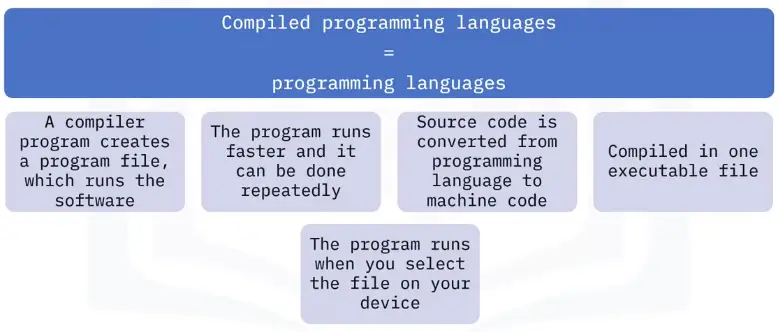
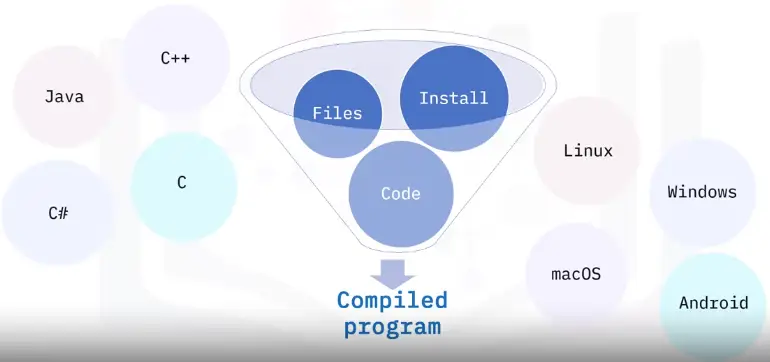
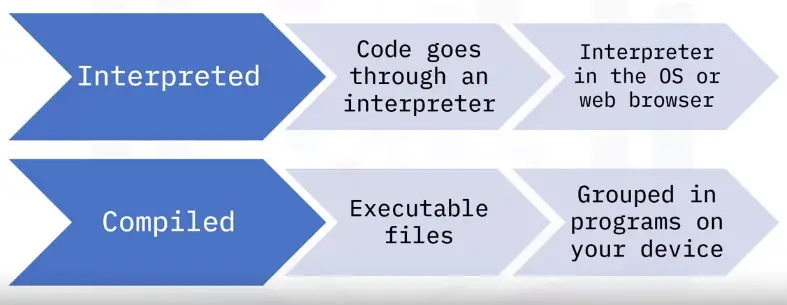
Networking Fundamentals
Network Topologies, Types, and Connections
Types and Topologies
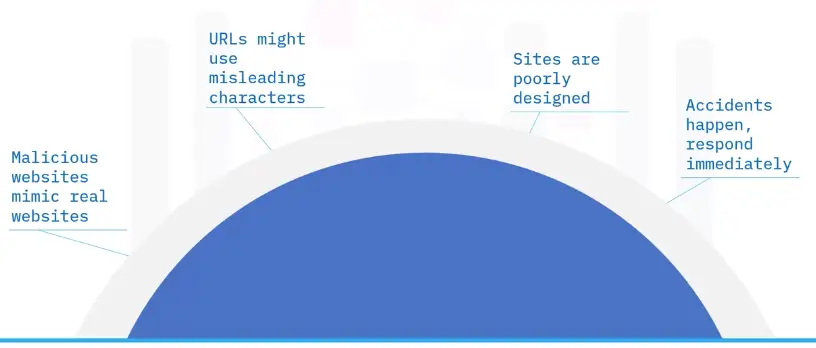
What is a computer network?
Computer networking refers to connected computing devices and an array of IoT devices that communicate with one another.
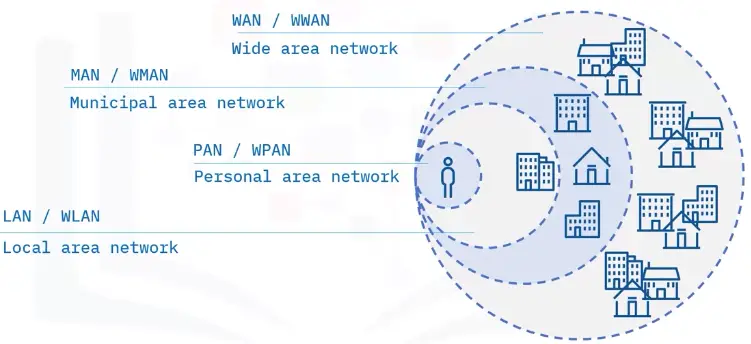
Network Types
There are multiple network types:
- PAN (Personal Area Network)
- LAN (Local Area Network)
- MAN (Metropolitan Area Network)
- WAN (Wide Area Network)
- WLAN (Wireless LAN)
- VPN (Virtual Private Network)
PAN (Personal Area Network)
A PAN enables communication between devices around a person. PANs can be wired or wireless.
-
USB
-
FireWire
-
Infrared
-
ZigBee
-
Bluetooth
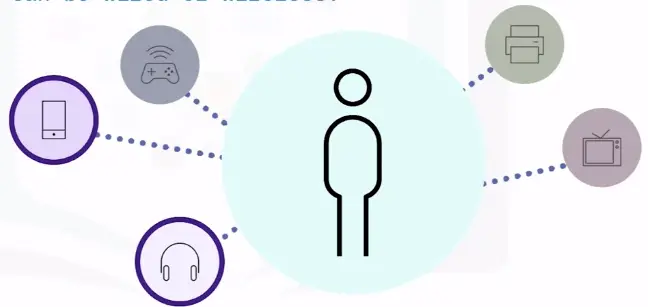

LAN (Local Area Network)
A LAN is typically limited to a small, localized area, such as a single building or site.
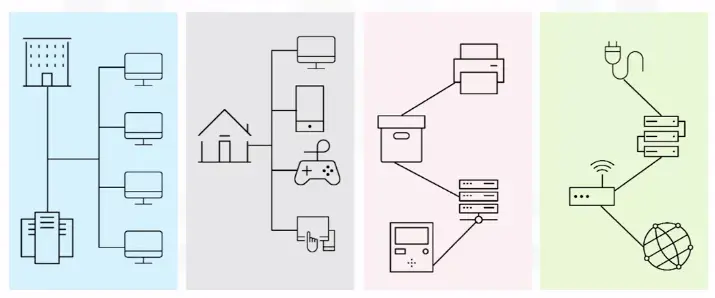

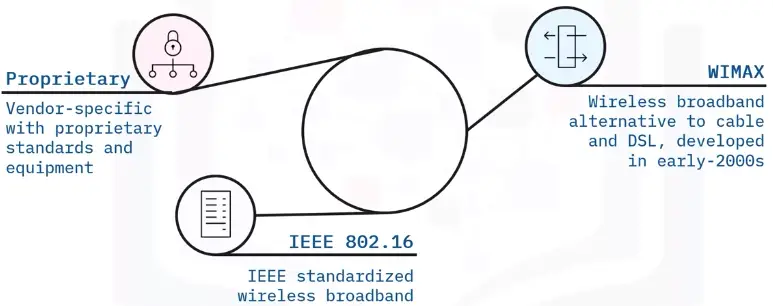
MAN (Metropolitan Area Network)
-
A MAN is a network that spans an entire city, a campus, or a small region.
-
MANs are sometimes referred to as CANs (Campus Area Networks).
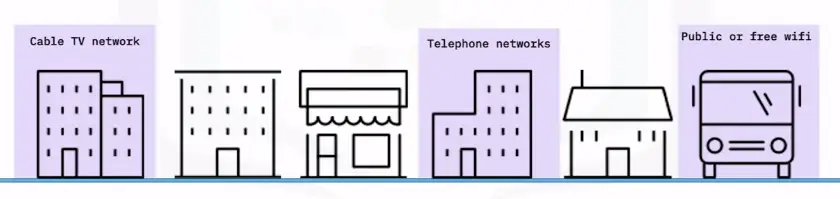

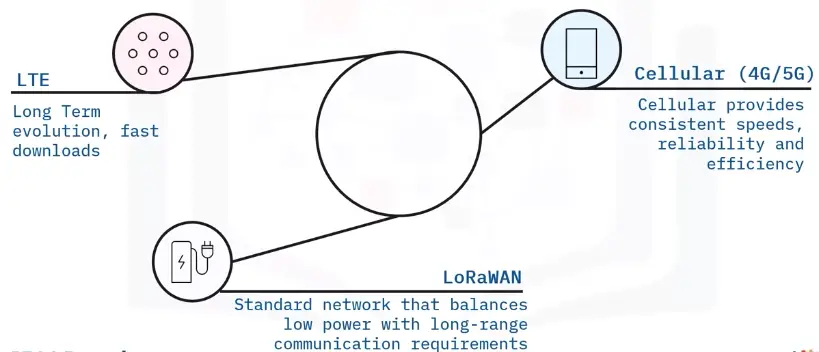
WAN (Wide Area Network)
A WAN is a network that extends over a large geographic area.
-
Businesses
-
Schools
-
Government entities
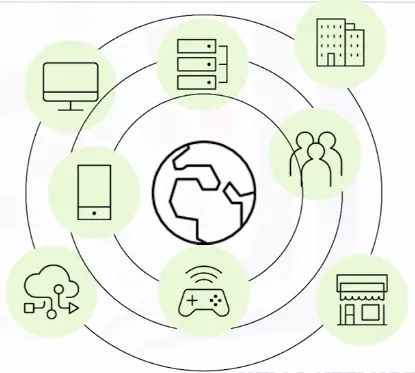

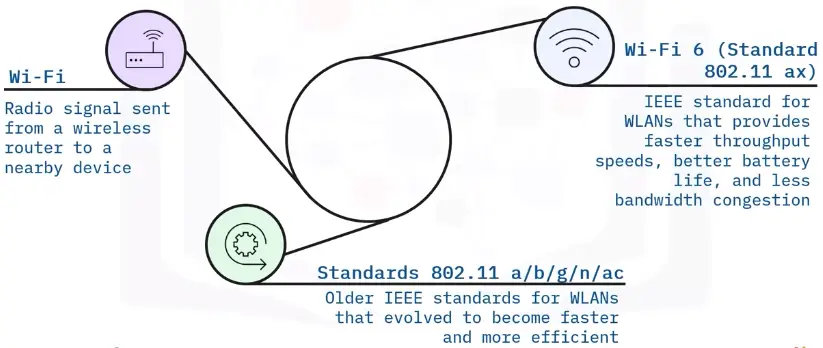
WLAN (Wireless LAN)
A WLAN links two or more devices using wireless communication.
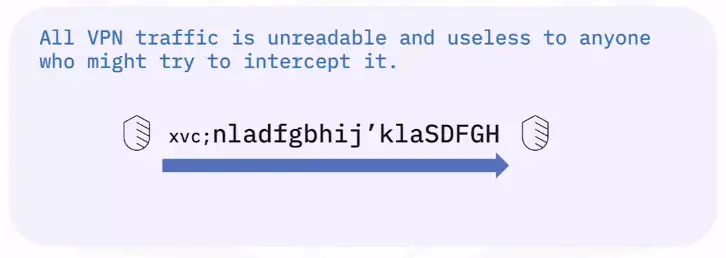
VPN (Virtual Private Network)
- A private network connection across public networks.
- Encrypt your Internet traffic.
- Disguise your online identity
- Safeguard your data.
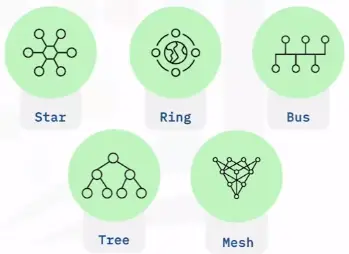
Topology
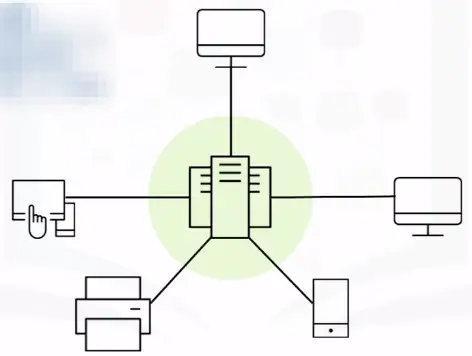
Star topology
Star topology networks feature a central computer that acts as a hub.

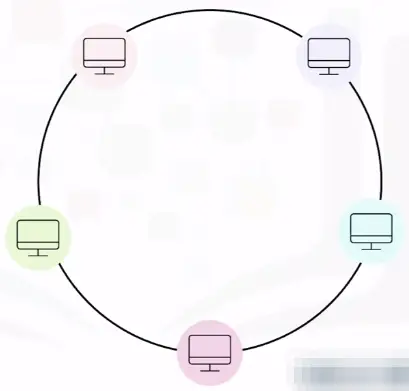
Ring topology
Ring topology networks connect all devices in a circular ring pattern, where data only flows in one direction (clockwise).

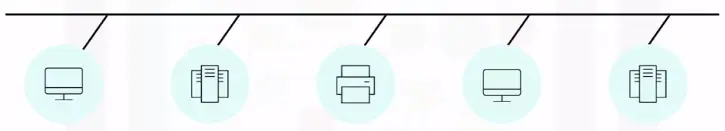
Bus topology
Bus topology networks connect all devices with a single cable or transmission line.
-
Small networks, LAN.

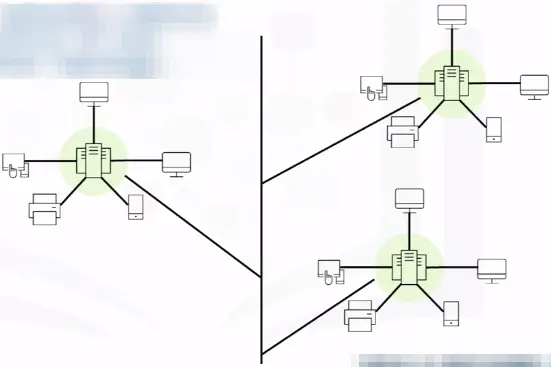
Tree topology
Tree topology networks combine the characteristics of bus topology and star topology.
-
University campus

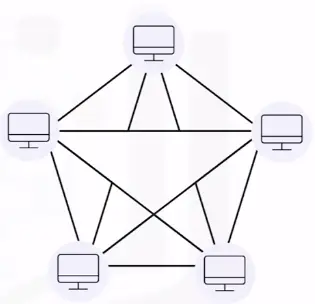
Mesh topology
Mesh topology networks connect all devices on the network together.
-
This is called dynamic routing.
-
It is commonly used in WAN network for backup purposes.
-
It is not used in LAN implementations.

Wire Connections
Older Internet Connection Types

Newer Internet Connection Types


Wired Networks
Wired networking refers to the use of wire connections that allow users to communicate over a network.
- Most computer networks still depend on cables or wires to connect devices and transfer data.
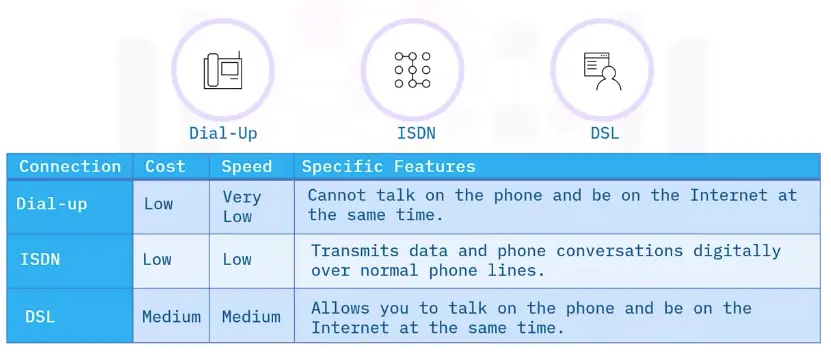
Wire Connections: Dial-Up
Requires a modem and phone line to access the internet.
Pros:
Wire Connections: DSL
Connects to the Internet using a modem and two copper wires within the phone lines to receive and transmit data.
Pros:
-
Faster than dial-up
-
Inexpensive
-
Dedicated connection (no bandwidth sharing)
-
Can provide Wi-Fi
-
Uses existing phone lines
Cons:
-
Slow speeds (less than 100 Mbps)
-
Not always available
Wired Connections: Cable
Cable delivers Internet via copper coaxial television cable.
Pros:
Wired Connection: Fiber Optic
Transmit data by sending pulses of light across strands of glass (up to 200 Gbps).
Pros:
-
Efficient
-
Reliable
-
Covers long distances
-
Fast speeds
-
Streaming and hosting
Cons:
-
Expensive
-
Not available everywhere
Cables
Cables types
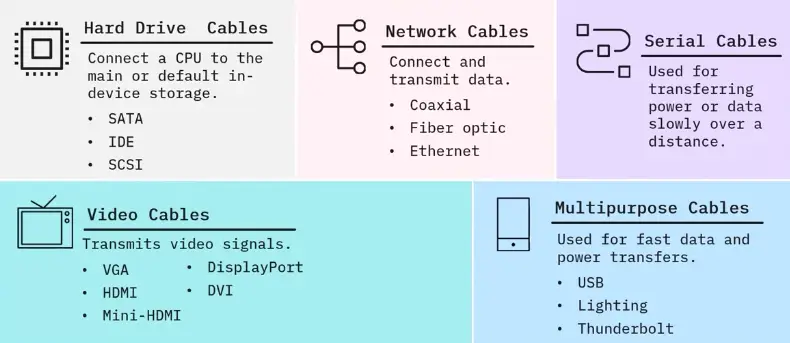

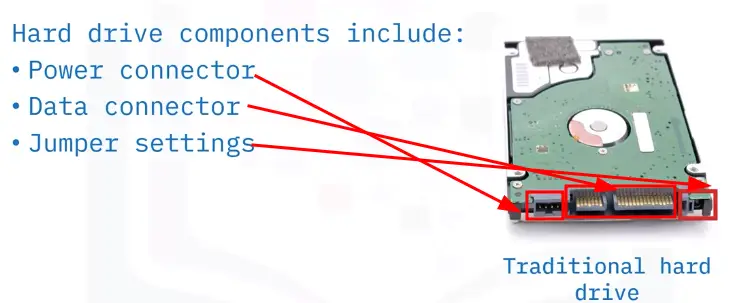
Hard Drive Cables
Hard drive cables connect a hard drive to a motherboard or controller card. May also be used to connect optical drives or older floppy drives.
- SATA
- Next-generation
- Carries high-speed data
- Connects to storage devices
- IDE
- Older tech
- 40-wire ribbon
- Connect motherboard to one or two drives
- SCSI
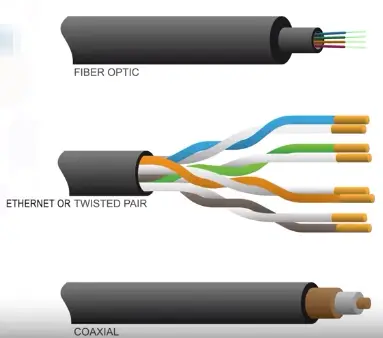
Network Cables
In wired networks, network cables connect devices and route information from one network device to another.
Cable need is determined by:
-
Network topology
-
Protocol
-
Size
Types:
-
Coaxial
- TV signals to cable boxes
- Internet to home modems
- Inner copper wire surrounded by shielding
- Highly Resistant to signal interference
- Supports greater cable lengths between devices
- 10 Mbps capacity, uses DOCSIS standard
-
Fiber optic
- Work over long distances without much interference
- Handles heavy volumes of data traffic
- Two Types
- Single-Mode
- Carries one light path
- Sourced by a laser
- Longer transmission distance
- Multimode
- Multiple light paths
- Sourced by an LED
-
Ethernet
- Consist of four pairs of twisted wires
- Reduce interference
- Wire a computer to LAN
- Fast and Consistent
- Two Types:
- Unshielded Twisted Pair (UTP)
- Shielded Twisted Pair (STP)
Serial Cables
A serial cable follows the RS-232 standard:
“Data bits must flow in a line, one after another, over the cable.”
Used in:
-
Modems
-
Keyboards
-
Mice
-
Peripheral devices


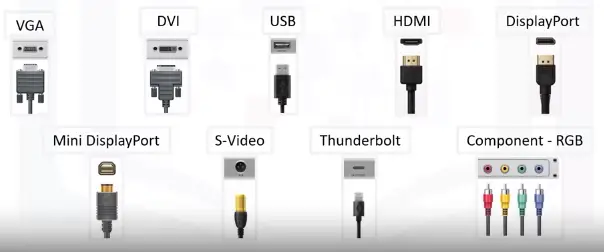
Video Cables
Transmits video signals.
- VGA
- DisplayPort
- Connects interface to display
- HDMI
- High definition
- Different connector types
- Type A is common
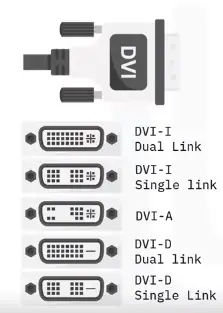
- DVI
- Can be digital or integrated
- Can be single or dual link
- Mini-HDMI
-
Type C HDMI


Multipurpose Cables
Multipurpose cables connect devices and peripherals without a network connection. They transfer both data and power.
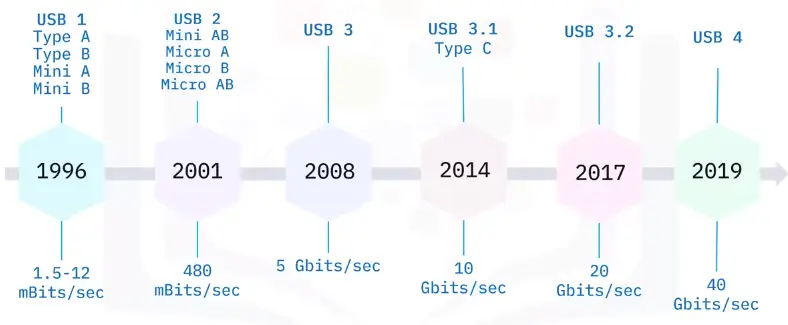
- USB
- Low speed 1.5 Mbps @3 meters
- Full speed 12 Mbps @5 meters
- Lighting
- Apple only
- Connects to USB ports
- Thunderbolt
- Apple only
- Copper max length 3 meters
- Optical max length 60 meters
- 20-40 Gbps throughput
Wireless Connections
Wireless network types

WPAN networking examples
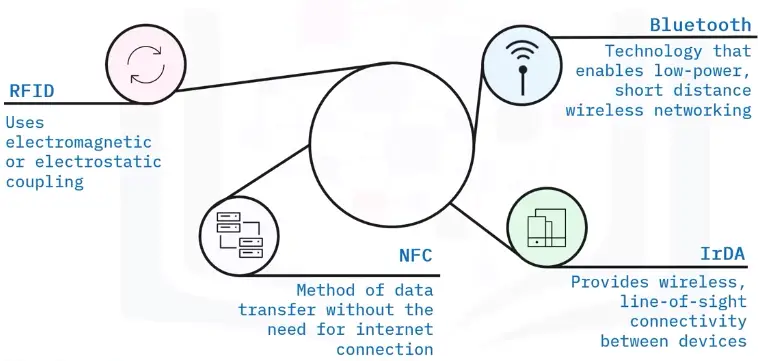

WLAN networking examples

WMAN networking examples

WWAN networking examples

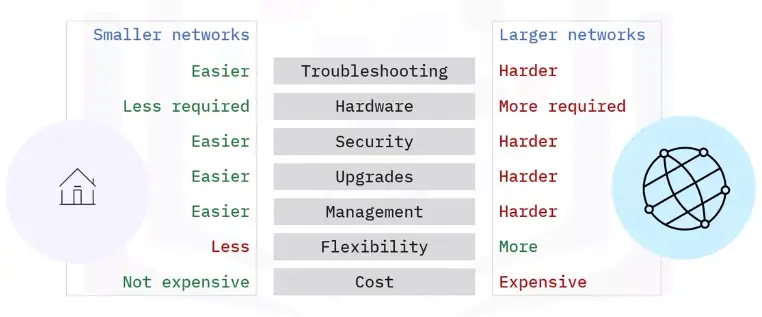
Wired vs. wireless
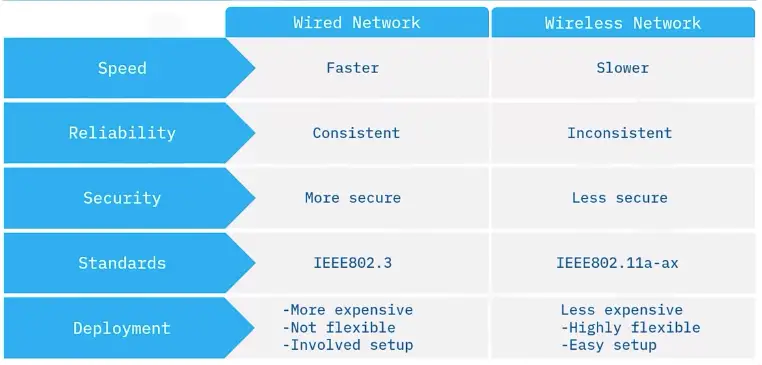

Latest Networking Trends
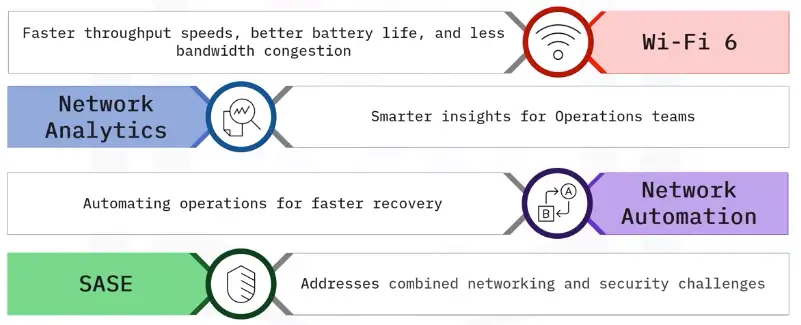

Advantages and Disadvantages of Network Types
Networks vs. devices
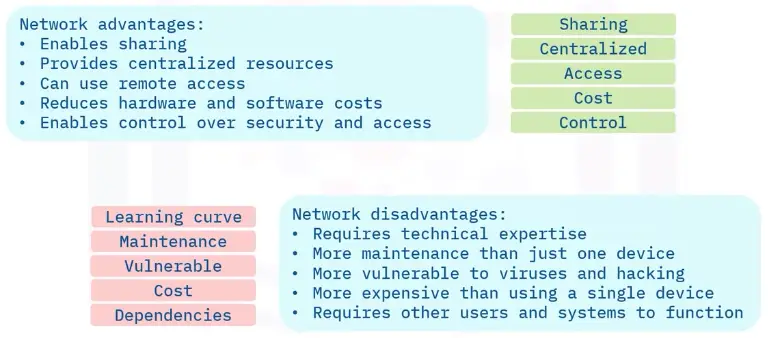

Smaller vs. larger

Wired vs. wireless
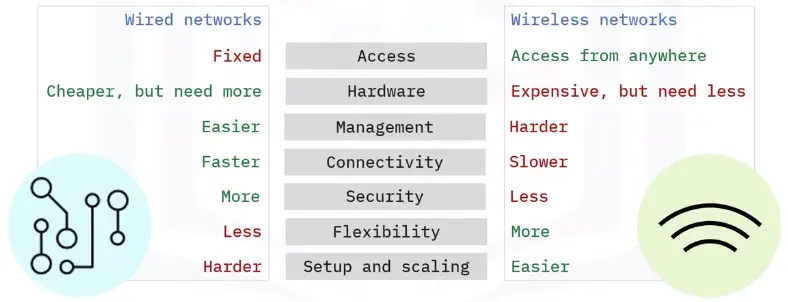

Network Types
Basic network types are:
-
Wired
-
Wireless

PAN
A PAN enables communication between devices around a person. PANs are wired and WPANs are wireless.
Advantages:
-
Flexible and mobile
-
One-time, easy setup
-
Portable
Disadvantages:
-
Limited range
-
Limited bandwidth
LAN
Advantages:
-
Reliable and versatile
-
Higher data transmission rates
-
Easier to manage
Disadvantages:
-
Smaller network coverage area
-
Number of device affects speed
-
Security risks
MAN
A MAN is optimized for a larger geographical area, ranging from several building blocks to entire cities.
Advantages:
-
Cover multiple areas
-
Easy to use, extend, and exchange
-
Managed by an ISP, government entity, or corporation
Disadvantages:
-
Requires special user permissions
-
Security risk
WAN
WANs and WWANs provide global coverage. Examples include the Internet and cellular networks.
Advantages:
-
Global coverage
-
More secure
Disadvantages:
-
Expensive
-
Difficult to maintain
Hardware, Network Flow, and Protocols
Networking Hardware Devices
Network Devices
Network devices, or networking hardware, enable communication and interaction on a computer network.
This includes:
- Cables
- Servers
- Desktops
- Laptops
- Tablets
- Smartphones
- IoT devices
What is a server?
- Other computers or devices on the same network can access the server
- The devices that access the server are known as clients
- A user can access a server file or application from anywhere
What are nodes and clients?
A node is a network-connected device that can send and receive information.
- All devices that can send, receive, and create information on a network are nodes.
- The nodes that access servers to get on the network are known as clients.
Client-server
Client-server networks are common in businesses.
-
They keep files up-to-date
-
Easy-to-find
-
One shared file in one location
Examples of services that use client-server networks:
-
FTP sites
-
Web servers
-
Web browsers
Peer-to-peer
Peer-to-peer networks are common in homes on the Internet.
Examples:
- File sharing sites
- Discussion forums
- Media streaming
- VoIP services
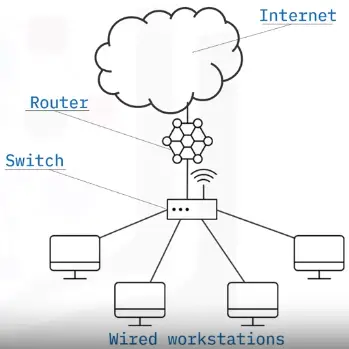
Hubs and Switches
A hub:
-
Connects multiple devices together
-
Broadcasts to all devices except sender
A switch:
-
Keeps a table of MAC addresses
-
Sends directly to correct address (More efficient than hubs)
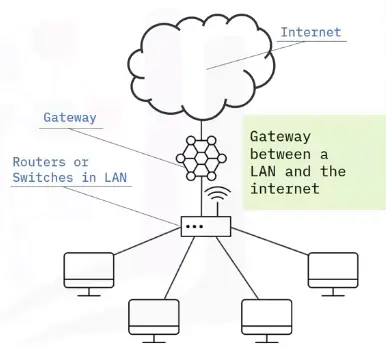
Routers and modems
Routers interconnect different networks or subnetworks.
-
Manage traffic between networks by forwarding data packets
-
Allow multiple devices to use the same Internet connection
Routers use internal routing to direct packets effectively
The router:
-
Reads a packet’s header to determine its path
-
Consults the routing table
-
Forwards the packet
A modem converts data into a format that is easy to transmit across a network.
-
Data reaches its destination, and the modem converts it to its original form
-
Most common modems are cable and DSL modems
Bridges and gateways
A bridge joins two separate computer networks, so they can communicate with each other and work as a single network.
Wireless bridges can support:
Repeaters and WAPs
Repeaters
-
Receive a signal and retransmits it
-
Used to extend a wireless signal
-
Connect to wireless routers
Wireless Access Point (WAP)
-
Allows Wi-Fi devices to connect to a wired network
-
Usually connects to a wired router as a standalone device
-
Acts as a central wireless connection point for computers equipped with wireless network adapters
Network Interface Cards (NICs)
NICs connect individual devices to a network.

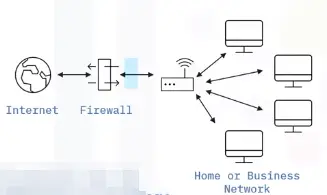
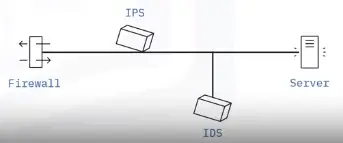
Firewalls, proxies, IDS, and IPS
A firewall monitors and controls incoming and outgoing network traffic based on predetermined security rules.
-
Firewalls can be software or hardware
-
Routers and operating systems have built-in firewalls

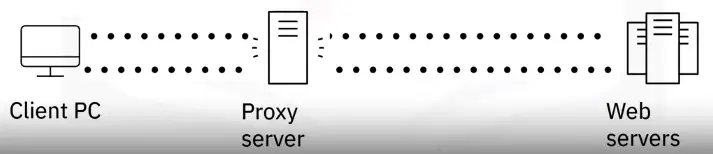
A Proxy Server:
-
Works to minimize security risks
-
Evaluates requests from clients and forwards them to the appropriate server
-
Hides an IP address
-
Saves bandwidth
IDS and IPS:
-
IDS monitors network traffic and reports malicious activity
-
IPS inspects network traffic and removes, detains, or redirects malicious items

Packets, IP Addressing, DNS, DHCP, and NAT
What is a packet?
Everything you do on the Internet involves packets.
Packets are also called:
- Frames
- Blocks
- Cells
- Segments
Data Transmission Flow Types
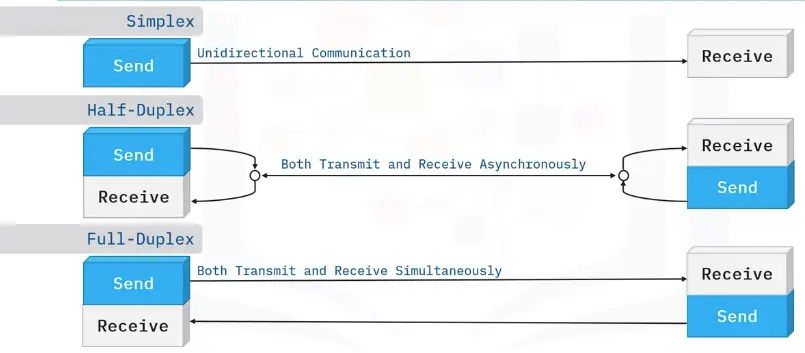

IP Packets Transmission Modes
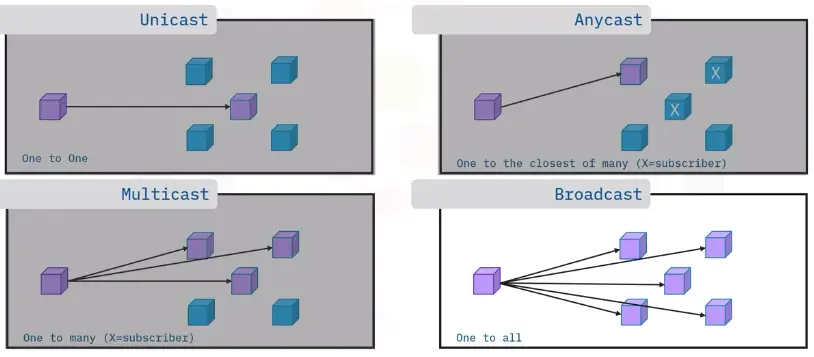

Data Transmission Flow
When you send an email, it is broken down into individually labeled data packets and sent across the network.
IPv4 and IPv6
- IPv4 is one of the core protocols for the Internet.
- IPv6 is the newest version of Internet Protocol.
What is an IP address?
An IP address is used to logically identify each device (Host) on a given network.
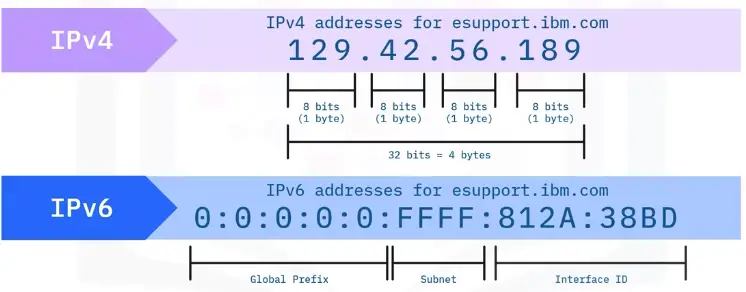

IP Address Types
Static: Static IP addresses are manually assigned.
Dynamic: Dynamic IP addresses are automatically assigned.
Public: Public IP address is used to communicate publically.
Private: Private IP address is used to connect securely within an internal, private network.
Loopback: Loopback is the range of IP addresses reserved for the local host.
Reserved: Reserved IP addresses have been reserved by the IETF and IANA.
DNS
The DNS is the phone book of the internet.
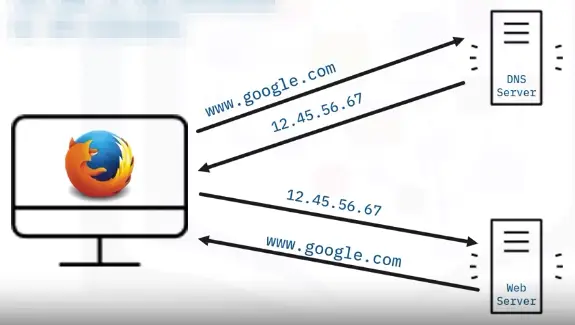

Dynamic Host Configuration Protocol (DHCP)
The DHCP automates the configuring of IP network devices.
A DHCP server uses a pool of reserved IP addresses to automatically assign dynamic IP addresses or allocate a permanent IP address to a device.
Static allocation:
The server uses a manually assigned “permanent” IP address for a device.
Dynamic allocation:
The server chooses which IP address to assign a device each time it connects to the network.
Automatic allocation:
The server assigns a “permanent” IP addresses for a device automatically.
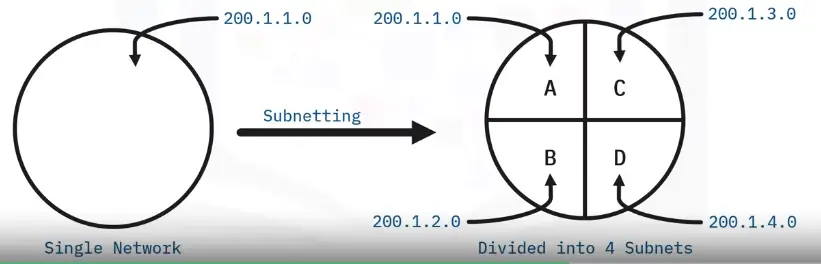
Subnetting (and Subnet Mask)
Subnetting is the process of taking a large, single network and splitting it up into many individual smaller subnetworks or subnets.
-
Identifies the boundary between the IP network and the IP host.
-
Internal usage within a network.
-
Routers use subnet masks to route data to the right place.

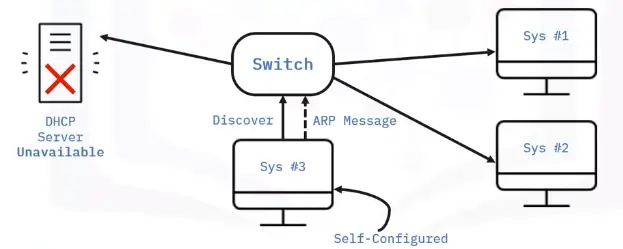
Automatic Private IP Addressing (APIPA)
APIPA is a feature in operating systems like Windows that let computers self-configure an IP address and subnet mask automatically when the DHCP server isn’t reachable.

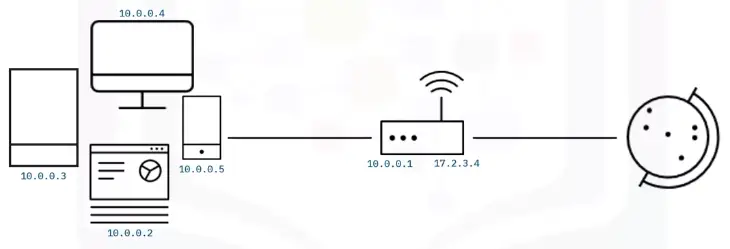
Network Address Translation (NAT)
NAT is a process that maps multiple local private addresses to a public one before transferring the information.
-
Multiple devices using a single IP address
-
Home routers employ NAT
-
Conserves public IP addresses
-
Improves security
NAT instructions send all data packets without revealing private IP addresses of the intended destination.

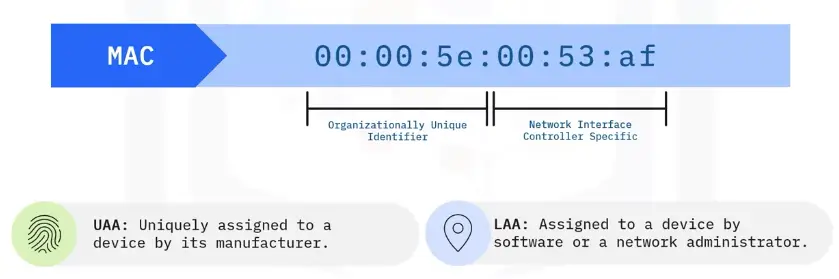
A MAC address is the physical address of each device on a network.

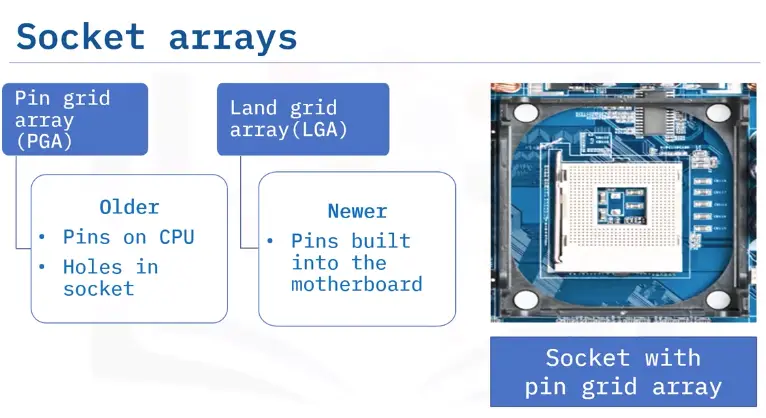
Models, Standards, Protocols, and Ports
Networking Models
A networking model describes:
-
Architecture
-
Components
-
Design
Two types:
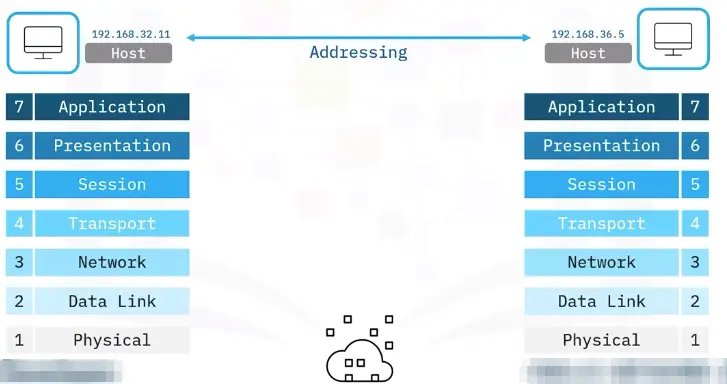
- OSI Model: A conceptual framework used to describe the functions of a networking system.
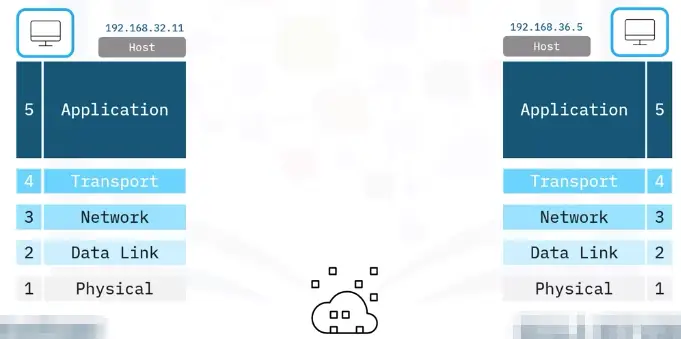
- TCP/IP Model: A set of standards that allow computers to communicate on a network. TCP/IP is based on the OSI model.
7 Layer OSI Model

5 Layer TCP/IP Model
The TCP/IP model is a set of standards that allow computers to communicate on a network. TCP/IP is based on the OSI model.

Network Standards and their Importance
Networking standards define the rules for data communications that are needed for interoperability of networking technologies and processes.
There are two types of network standards:
- De-jure or Formal Standards: Developed by an official industry or government body.
Examples: HTTP, HTML, IP, Ethernet 802.3d
- De-Facto Standards: De-facto standards result from marketplace domination or practice.
Examples: Microsoft Windows, QWERTY keyboard
Noted Network Standards Organizations
Standards are usually created by government or non-profit organizations for the betterment of an entire industry.
- ISO: Established the well known OSI reference networking model.
- DARPA: Established the TCP/IP protocol suit.
- W3C: Established the World Wide Web (WWW) standard.
- ITU: Standardized international telecom, set standards for fair use of radio frequency.
- IEEE: Established the IEEE 802 standards.
- IETF: Maintains TCP/IP protocol suites. IETF also developed RFC standard.
Protocols
A network protocol is a set of rules that determines how data is transmitted between different devices in the same network.
- Security:
- Encryption
- Authentication
- Transportation
- Communication:
- Encryption
- Authentication
- Transportation
- Network Management:
- Connection
- Link Aggregation
- Troubleshooting
Protocols – TCP vs. UDP
| TCP |
UDP |
| Slower but more reliable |
Faster but not guaranteed |
| Typical applications |
Typical application |
| 1) File transfer protocol |
1) Online games |
| 2) Web browsing |
2) Calls over the internet |
| 3) EMAIL |
|
Protocols – TCP/IP
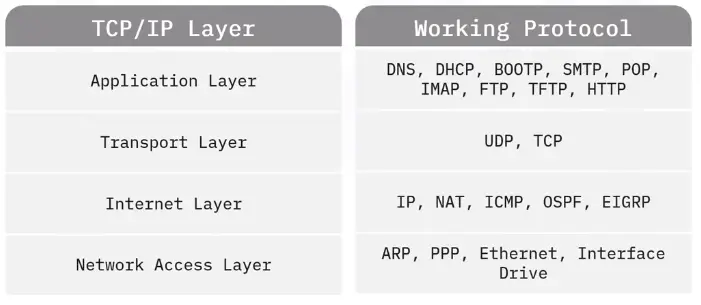
The TCP/IP suite is a collection of protocols.

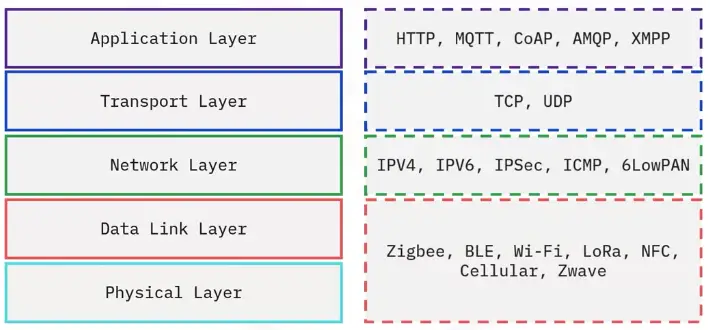
Protocols – Internet of Things

Protocols – Crypto Classic
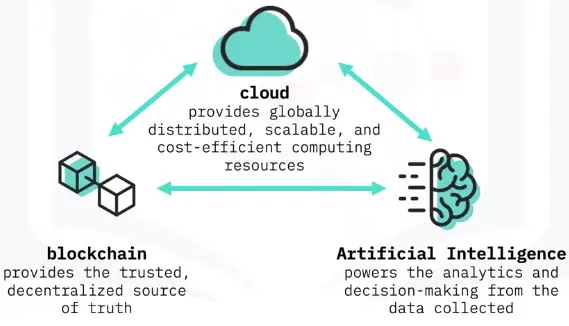
The Crypto Classic protocol is designed to serve as one of the most efficient, effective, and secure payment methods built on the blockchain network.
Bitcoin Protocol: A peer-to-peer network operating on a cryptographic protocol used for bitcoin transactions and transfers on the Internet.
Blockchain Protocol: An open, distributed ledger that can record transactions between two parties efficiently and in a verifiable and permanent way.
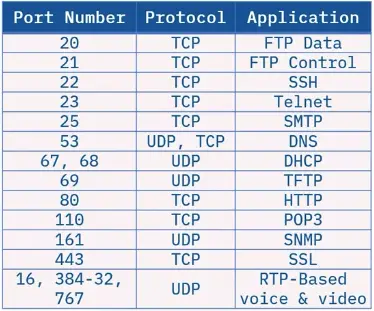
Commonly Used Ports
Ports are the first and last stop for information sent across a network.
-
A port is a communication endpoint.
-
A port always has an associated protocol and application.
-
The protocol is the path that leads to the application’s port.
-
A network device can have up to 65536 ports.
-
Port numbers do not change.

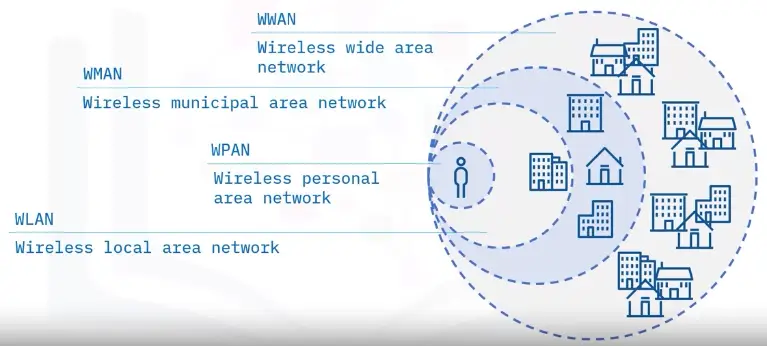
Wireless Networks and Standards
Network types

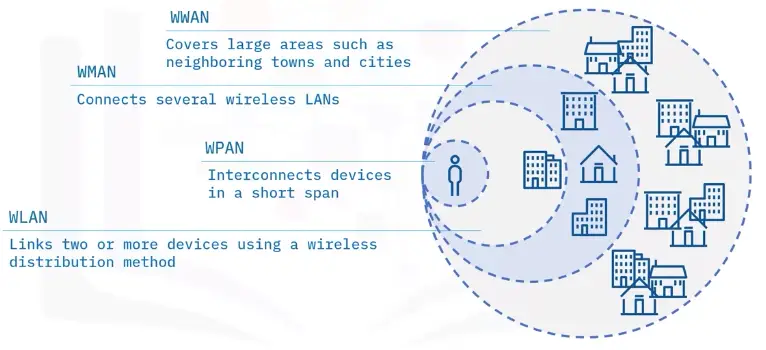
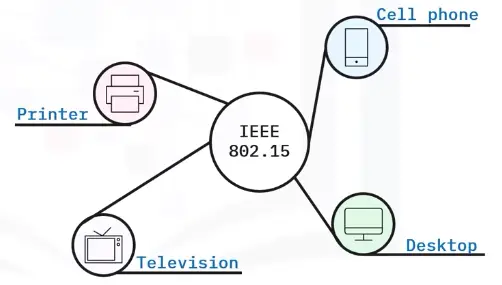
WPAN
A WPAN connects devices within the range of an individual person (10 meters). WPANs use signals like infrared, Zigbee, Bluetooth, and ultra-wideband.

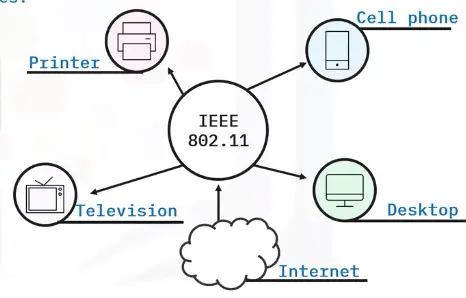
WLAN
A WLAN connects computers and devices within homes, offices, or small businesses. WLANs use Wi-Fi signals from routers, modems, and wireless access points to wirelessly connect devices.

WMAN
A WMAN spans a geographic area (size of a city). It serves ranges greater than 100 meters.

WWAN
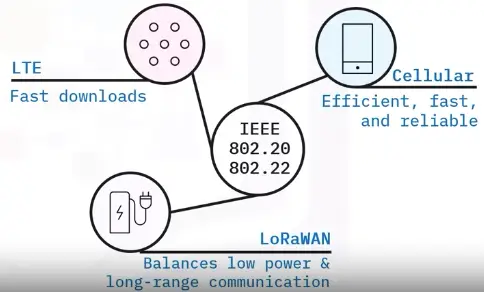
A WWAN provides regional, nationwide, and global wireless coverage. This includes private networks of multinational corporations, the Internet, and cellular networks like 4G, 5G, LTE, and LoRaWAN.

Wireless ad hoc network
A WANET uses Wi-Fi signals from whatever infrastructure happens to be available to connect devices instantly, anywhere. WANETs are similar in size to WLANs, but use technology that is closer to WWANs and cellular network.
Advantages:
-
Flexible
-
No required infrastructure
-
Can be set up anywhere instantly
Disadvantages:
-
Limited bandwidth quality
-
Not robust
-
Security risks

Cellular networks
A cellular network provides regional, nationwide, and global mesh coverage for mobile devices.

Advantages
-
Flexibility
-
Access
-
Speed and efficiency
Disadvantages
-
Expensive
-
Decreased coverage
-
Hardware limitations
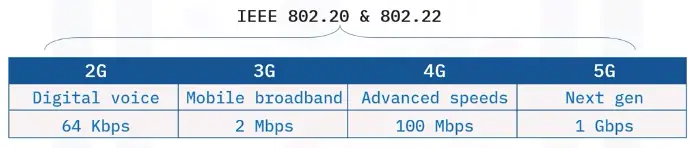
IEEE 802.20 and IEEE 802.22
The IEEE 802.20 and 802.22 standards support WWANs, cellular networks and WANETs.


IEEE 802.20
-
Optimizes bandwidth to increase coverage or mobility
-
Used to fill the gap between cellular and other wireless networks
IEEE 802.22
-
Uses empty spaces in the TV frequency spectrum to bring broadband to low-population, hard-to-reach areas
Protocol Table
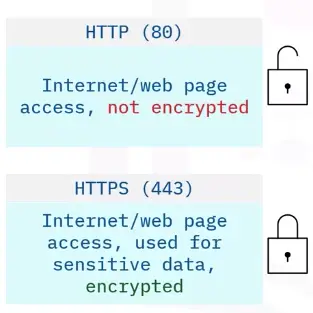
Web page protocols

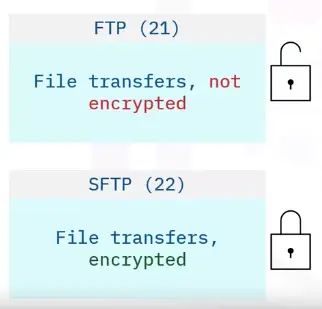
File transfer protocols

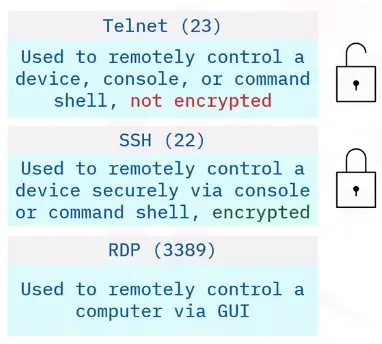
Remote access protocols

Email protocols


Network Protocols


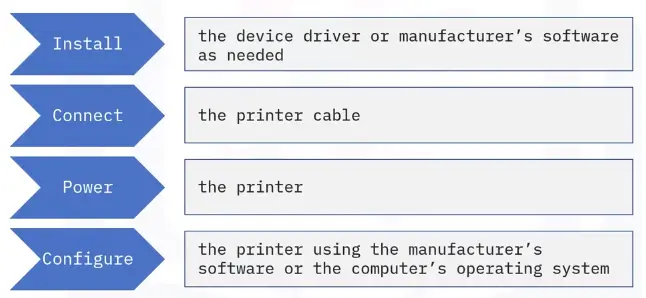
Configuring and Troubleshooting Networks
Configuring a Wired SOHO Network
What is a SOHO Network?
A SOHO (small office, home office) network is a LAN with less than 10 computers that serves a small physical space with a few employees or home users.
It can be a wired Ethernet LAN or a LAN made of both wired and wireless devices.
A typical wired SOHO network includes:
Setup steps – plan ahead
When setting up a SOHO network, knowing the compatibility requirements is very important.
Setup steps – gather hardware
-
SOHO networks need a switch to act as the hub of the network
-
If Internet is desired, a router can be added or used instead


Setup steps – connect hardware
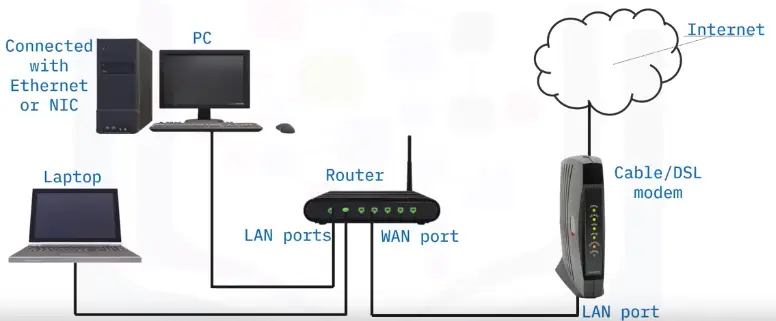

Setup steps – router settings
Log in to router settings
-
Enter ‘ipconfig’ in a command prompt window to find your router’s public IP address (listed next to default gateway)
-
Enter it into a browser and log in
Update username and password
-
All routers have default administrator usernames and passwords
-
To improve security, change the default username password
Update firmware
-
Updating router firmware solves problems and enhances security
-
Check the manufacturer website for available firmware updates
-
Download and install if your firmware is not up-to-date
Setup steps – additional settings
- SOHO wired network security depends on a firewall
- Most routers have a built-in firewall, additional software can be installed on individual machines
- Servers and hardware have built-in DHCP and NAT actions
- DHCP servers use IP addresses to provide network hosts
- NAT maps public IPv4 address to private IP addresses
Setup steps – user accounts
User account setup is included in most operating systems.
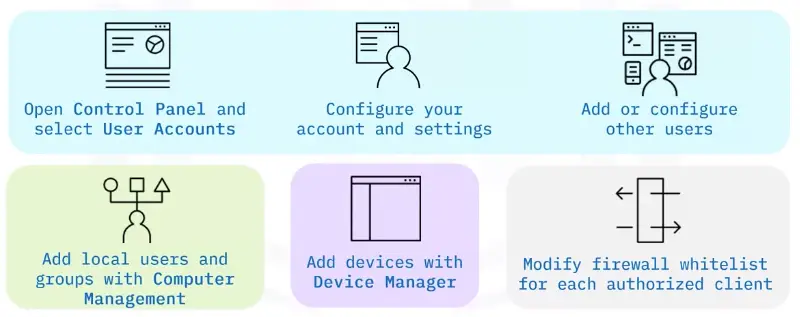

Setup steps – test connectivity
Network performance depends on Internet strength, cable specification, installation quality, connected devices, and network and software settings.
Test and troubleshoot to ensure proper network performance.
To troubleshoot performance:
- Run security tools
- Check for updates
- Restart devices
- Run diagnostic
- Reboot the router or modem
Configuring a (wireless) SOHO network
What is a SOHO wireless network?
A SOHO wireless network is a WLAN that serves a small physical space with a few home users.
A SOHO wireless network can be configured with the help of a central WAP, which can cover a range of wireless devices within a small office or home.
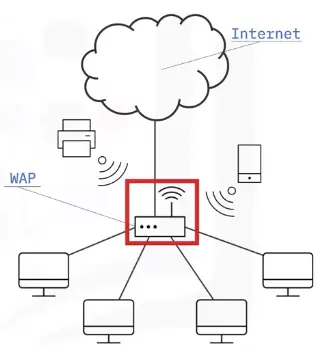

Common broadband types
Common broadband types that enable network connection:
- DHCP:
- The most common broadband type, used in cable modem connections.
- PPPoE:
- Used in DSL connections in areas that don’t have newer options.
- Static IP:
Wireless security factors
Wireless networks can be setup to be either open (unencrypted) or encrypted.
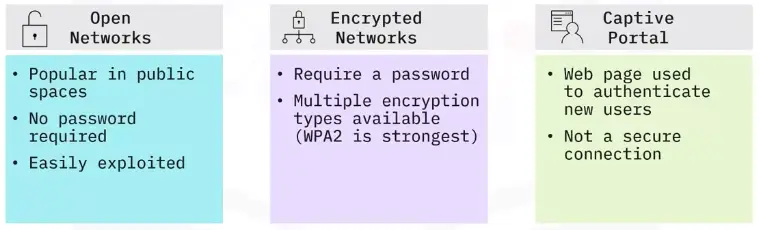

Get to know your wireless router
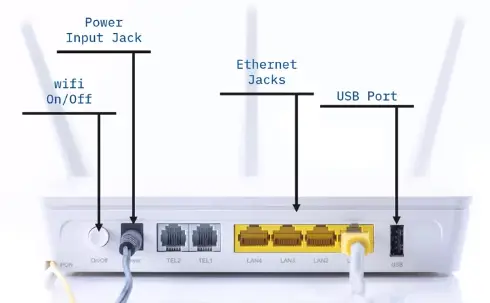

Connect to router admin interface
To manage router settings, you must find its default IP address, paste it into a browser and hit enter.
Assign a SSID
- SSID is the name of a wireless network.
- This name is chosen during setup.
- Unique names help to identify the network.
- Each country determines band and available modes.
- 2.4 GHz and 5 GHz have specific supported modes.
- Every router has as a default option.
Wireless encryption security modes
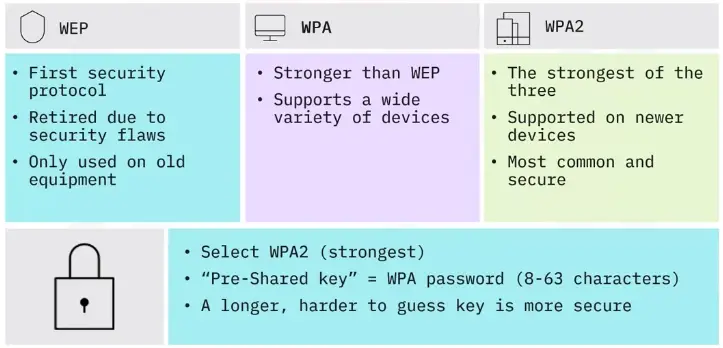

Going wireless
Once the router is configured, your wireless network is ready.
Users will see it among the available wireless networks when they click the Wi-Fi icon.
Test and troubleshoot connectivity
Test network performance and Internet connectivity on each wireless device in the vicinity of the WAP.
If required, troubleshoot performance issues (network lags, glitches, or network cannot be accessed) with the following actions:
- Check router configuration settings.
- Run security tools.
- Check for updates.
- Restart devices.
- Run diagnostics.
- Reboot the router or modem.
- Check equipment for damage.
Mobile configuration
IMEI vs. IMSI
IMEI and IMSI are used to identify cellular devices and network users when troubleshooting device and account issues.
Internation Mobile Equipment Identity (IMEI)
-
ID# for phones on GSM, UMTS, LTE, and iDEN networks
-
Can be used to block stolen phones
International Mobile Subscriber Identity (IMSI)
-
ID# for cell network subscribers
-
Stored in a network sim card
Troubleshooting Network Connectivity
Symptoms of connectivity problems
“Can’t connect” or “slow connection” are two of the most common network problems. These symptoms can be caused by several things.
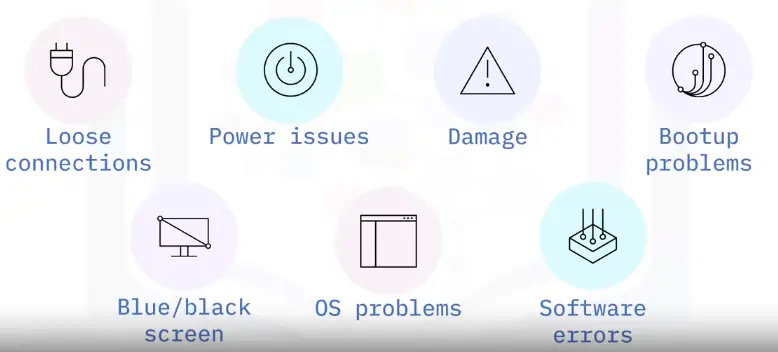
Causes of Connectivity Problems
Common causes of network connectivity problems:
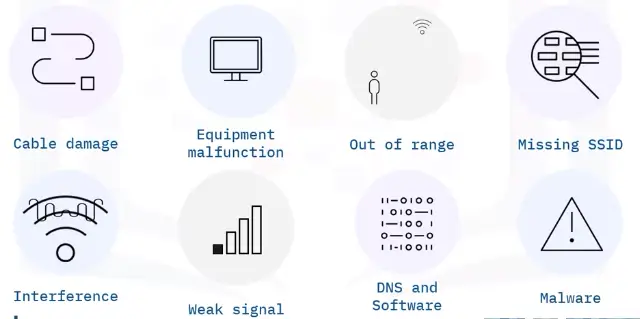

Cable Damage
Cable damage slows or stops network connections. The damage can be obvious or hidden from view.
Ways to solve:
- Check for physical damage
- Test the cable using different devices or a specialized tool
- Replace the cable
Equipment malfunction
An equipment malfunction can slow or stop network connections.
Ways to solve:
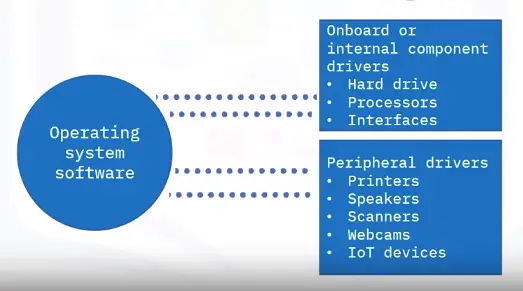
- Check network adapter drivers in Device Manager
- Check switch or router port settings in the management software
- Replace the equipment
Out of range
When a user is too far away from a wireless signal, their connection will lag or fail.
Ways to solve:
- Move physically closer to the source of the wireless connection
- Move the wireless connection source closer to the affected user(s)
- Use stronger devices to boost the signal strength
- Use more devices to ensure the Wi-Fi reaches users who are farther away
Missing SSID
Network connections can fail when a user can’t find the network name (SSID) in the available networks list.
Ways to solve:
- Move physically closer to the Wi-Fi source
- Reconfigure the network to ensure the SSID is not hidden
- Upgrade devices or use compatibility mode on newer network, so older devices can still connect
- Compatibility mode can slow a network
- Reserve 2.4 GHz band for legacy devices
Interference
Interference is when a radio or microwave signal slows or breaks a wireless connection.
Ways to solve:
- Remove the source of the interference signal
- Use a different Wi-Fi frequency (wireless)
- Use shielded cables to connect (wired)
- Remodel the building with signal-blocking materials
Weak signal strength
When signal strength is weak, a wireless adapter might slow speeds down to make the connection more reliable.
Weak signals cause:
DNS and software configuration
Network connections can fail when DNS or software is configured incorrectly.
DNS issue:
-
Domain not recognized
-
IP addresses recognized
OS and apps issue:
-
Software affecting connection
Ways to solve:
-
For DNS servers, test domains using ipconfig in a command prompt
-
For apps and OSes, use the network troubleshooter in Windows Settings
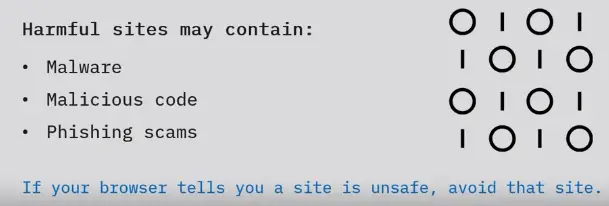
Malware
Malware slows or stops network connections intentionally, or as a result of overloading a system with other tasks.
Ways to solve:
- Use antimalware tools
- Adjust firewall settings
- Configure Privacy settings
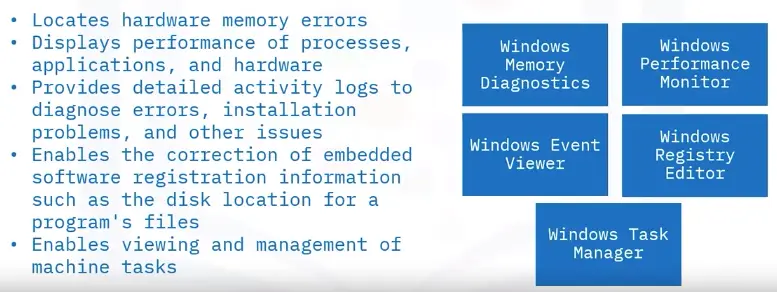
Network Troubleshooting with Command Line Utilities
Common command line utility commands that you would use to troubleshoot or diagnose network issues:
- ipconfig
- IP address
- Subnet mask
- Default gateway
- ping
- nslookup
- It lists:
- Your DNS server
- Your DNS server’s IP address
- Domain name
- tracert
- Tracert lists:
- Sent from
- Sent to
- Number of transfers
- Transfer locations
- Duration
- netstat: It shows if a server’s email and ports are open and connecting to other devices.
- Netstat lists:
- Protocol
- Local address
- Foreign address
- Current state
Storage Types and Network Sharing
Types of Local Storage Devices
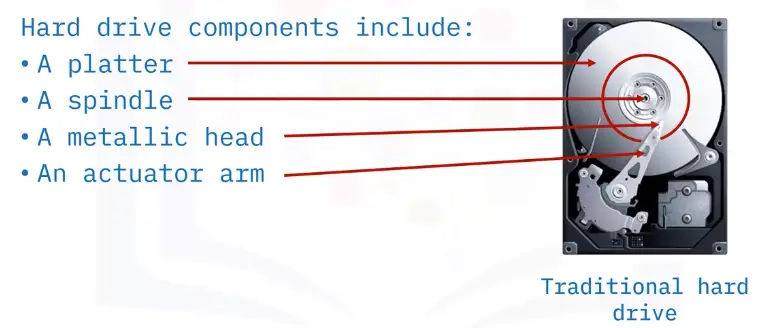
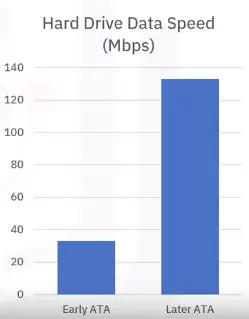
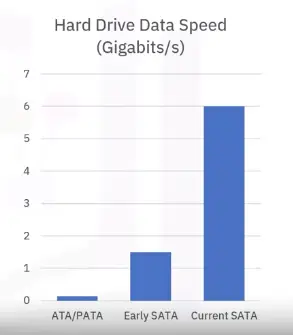
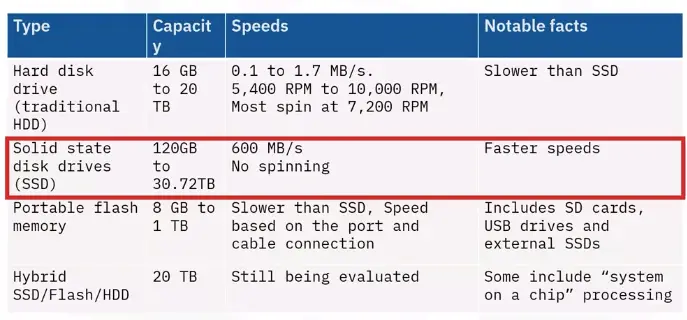
Hard Drive (HD or HDD)
HDDs:
- Large storage capacity
- Up to 200 MB/s
- Can overheat
- Were the standard PC storage for decades
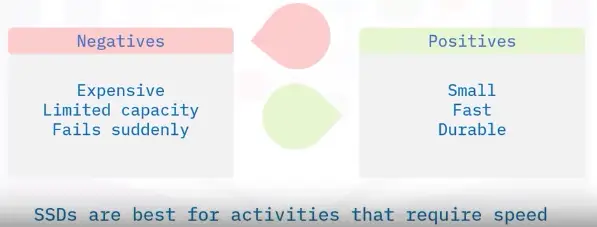
Solid-state Drive (SSD)
Solid-state Hybrid Drive (SSHD)
SSHDs integrate the speed of an SSD and the capacity of an HDD into a single device. It decides what to store in SSD vs. HDD based on user activity.
SSHDs are:
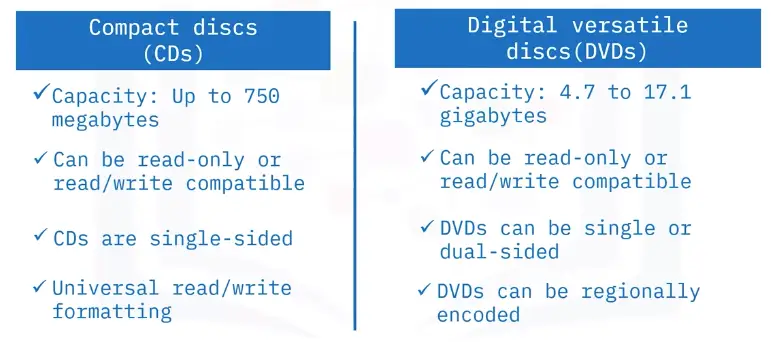
Optical Disk Drive (ODD)
ODDs are also called:
- CD Drives
- DVD Drives
- BD Drives
- Disc Drives
- Optical Drives
Flash Drive
Flash drives store data on solid-state drives (SSDs). Less energy is needed to run flash drives, as they don’t have moving parts that require cooling. High-end versions deduplicate and compress data to save space.


Local Storage wit Multiple Drives
Hybrid disk arrays physically combine multiple SSD and HDD devices into an array of drives working together to achieve the fast and easy performance of solid-state and the lower costs and higher capacities of hard-disk.


Direct Attached Storage (DAS)
DAS is one or more storage units within an external enclosure that is directly attached to the computer accessing it.


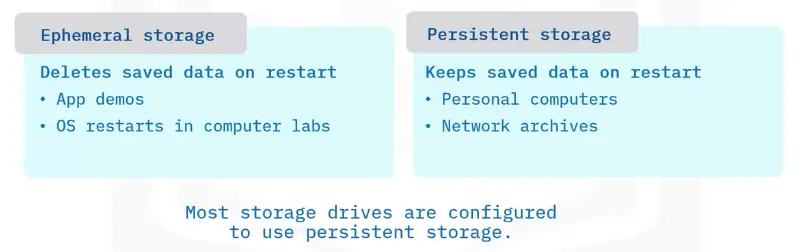
Ephemeral and Persistent storage
In DAS units and other storage devices, you can configure storage settings to be Ephemeral or Persistent.

Redundant Array of Independent Disks (RAID)
A RAID spread data across multiple storage drives working in parallel.




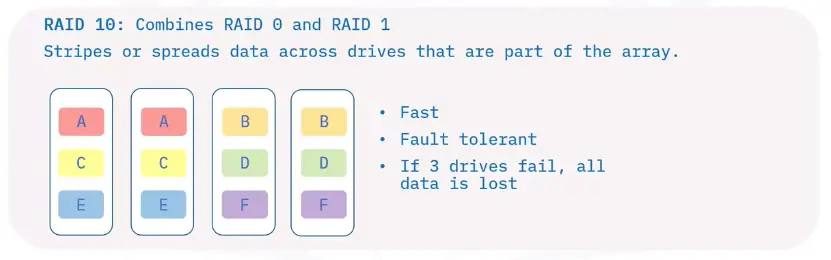

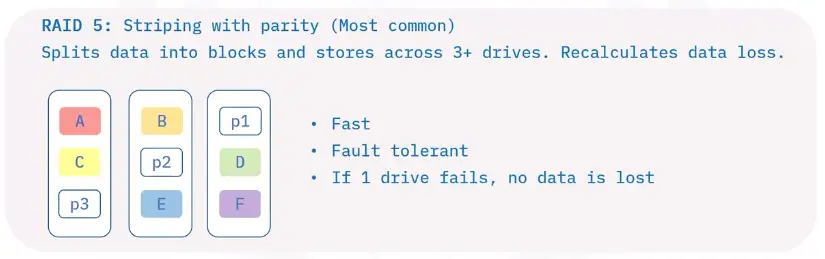

Companies choose RAID devices for their durability and performance.
- Maintain RAID devices
- Keep spare drives
- Perform routine backups
Troubleshooting Storage Issues
Disk Failure symptoms
Disk failure can be caused by wear and tear over time, faulty manufacturing, or power loss.
- Read/write failure
- Blue screen of Death (BSoD)
- Bad sectors
- Disk thrashing
- Clicking and grinding noises
Chkdsk and SMART
The chkdsk tools and the SMART program are used to monitor and troubleshoot disk health.
SMART: Self-Monitoring Analysis, and Reporting Technology
-
wmic/node: localhost diskdrive get status
Check disk tools
-
chkdsk /r locates bad sectors
-
chkdsk /f attempts to fix file system errors
Boot failures
When a computer fails to boot:
Computer power up
-
Lights and sound
-
Plugged in
Drive configuration
-
Correct firmware boot sequence
-
No removable disks
-
Cables connected and undamaged
-
Motherboard port enables
Filesystem error
Boot into recovery and enter C: in command prompt.
-
If invalid media type, reformat disk with bootrec tool (erases all data).
-
If invalid drive specification, partition structure with diskparttool.
Boot block repair
Errors like “Invalid drive specification” or “OSS not found” indicate boot errors (caused by disk corruption, incorrect OS installation, or viruses).
- Try antivirus boot disk and recovery options
- Original product disk > Repair
- Startup repair
- Command prompt
- Fix MBR:
bootrec /fixmbr
- Fix boot sector:
bbotrec /fixboot
- Correct missing installation in BCD:
bootrec /rebuild bcd
File recovery options
For computers that won’t boot, you can try to recover files by removing the hard drive and connecting it to another computer.
Recovery options:
- Windows disk management
- chkdsk
- Third-Party file recovery
Disk performance can slow if a disk is older, too full, or its files are not optimized.
To improve performance:
- Defragment the drive
- Add RAM
- Upgrade to a solid state or hybrid drive
- Remove files and applications
- Add additional drive space
Troubleshooting optical drives
Optical drives are laser-based and don’t physically touch disks.
-
Cleaning kits solve read/write errors
-
CD-ROM drives cannot play DVDs and Blu-rays
-
DVD and Blu-ray drives have third-party support
-
Writable discs have recommended write speeds
Buffer underrun
When the OS is too slow for the optical drive’s write process, errors occur.
To fix buffer underrun:
-
Use latest writes
-
Burn at lower speeds
-
Close apps during burn
-
Save to hard drive instead
Troubleshooting RAID issues
Here are some common RAID troubleshooting steps:
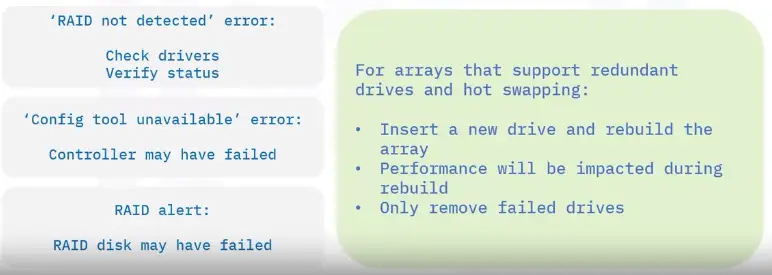

Types of Hosted Storage and Sharing
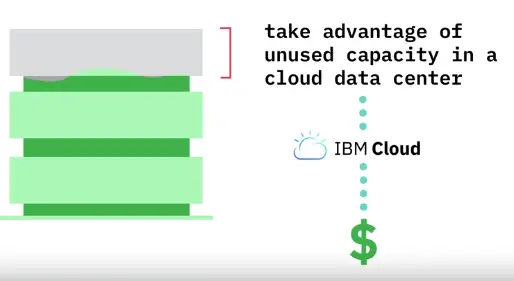
Storage as a Service (STaaS)
STaaS is when companies sell network storage space to customers, so they don’t have to buy and maintain their own network equipment.
- Dropbox
- OneDrive
- Google Drive
- box
- Amazon Drive
Email
Companies store your data, emails, and attachments in their data centers.
Social Media
Companies store your photos, videos, and messages in their data centers.
- Gmail waits 30 days before permanent removal.
- Facebook deleted after 90 days, but keeps certain user data indefinitely.
Workgroup and homegroup
A workgroup or homegroup is a group of computers on a SOHO network, typically without a server.
-
To share files and folders, users set them to ‘public’
-
Data is stored on the user device that created it.
-
The added points of failure create higher risk of data loss.
-
Newer cloud solutions provide the same features more securely.
Workgroups and homegroups are less common. Homegroups have been removed from Windows 10 altogether.
Repositories
A repository is a network location that lets a user store, manage, track, collaborate on, and control changes to their code.
Repositories save every draft. Users can roll things back if problems occur. This can save software developers months of time.
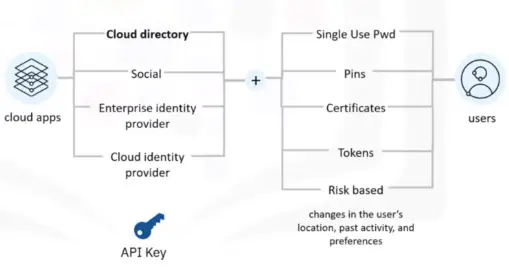
Active Directory Domain Service (AD DS)
AD is a Microsoft technology that manages domain elements such as users and computers.
-
Organizes domain structure.
-
Grants network access.
-
Connects to external domains.
-
It can be managed remotely from multiple locations.
Active Directory Domain Services:
-
Stores centralized data, manages communication and search.
-
Authenticates users so they can access encrypted content.
-
Manages single-sign on (SSO) user authentication.
-
Limits content access via encryption.
Network drives
Network drives are installed on a network and shared with selected users. They offer the same data storage and services as a standard disk drive.
- Network drives can be located anywhere.
- Network drives appear alongside local drive.
- Network drives can be installed on computers, servers, NAS units, or portable drives.
Network file and print sharing
File and Printer Sharing is part of the Microsoft Networks services.
- Appear alongside local drives
- Accessed via a web browser
- Appears in the printer options
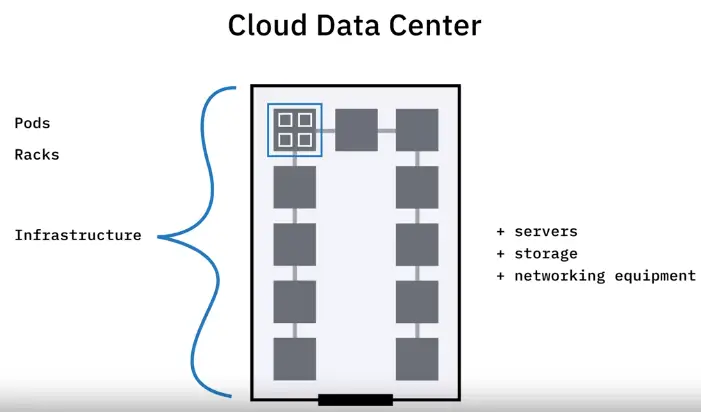
Network Storage Types
Network storage is digital storage that all users on a network can access.
- Small networks might rely on a single device for the storage needs of 1–5 people.
- Large networks (like the Internet) must rely on hundreds of datacenters full of servers.
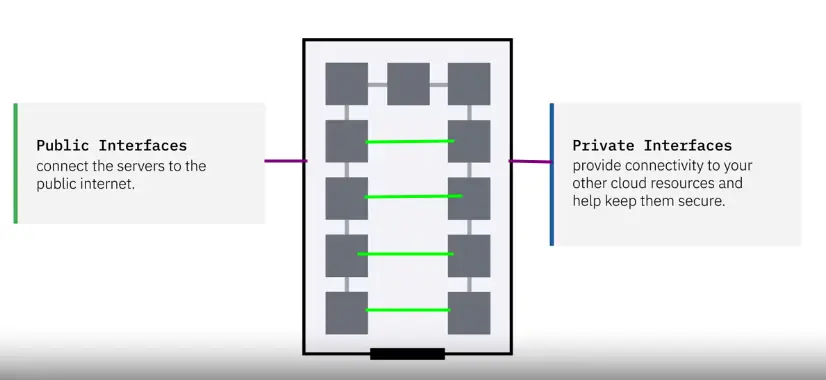
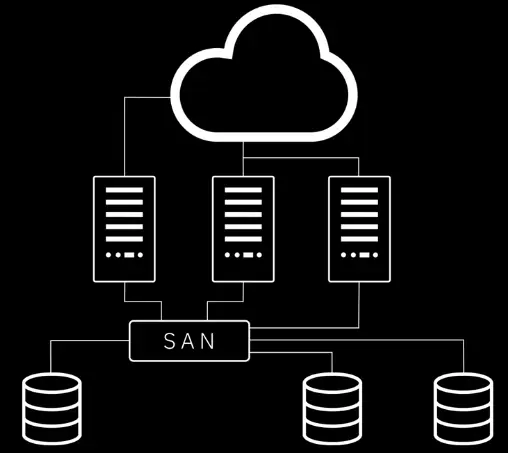
Storage Area Network (SAN)
A SAN combines servers, storage systems, switches, software, and services to provide secure, robust data transfers.
- Better application performance.
- Central and consolidated.
- Offsite (data protected and ready for recovery)
- Simple, centralized management of connections and settings.
Network Attached Storage (NAS)
A NAS device is a local file server. It acts as a hard drive for all devices on a local network.
- Convenient sharing across network devices.
- Better performance through RAID configuration.
- Remote Access
- Work when the Internet is down.
Difference between NAS and SAN
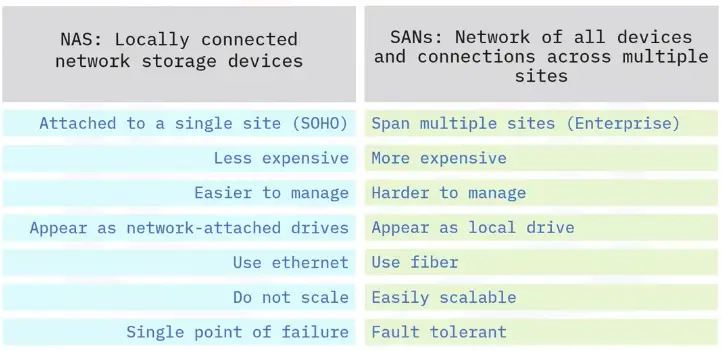

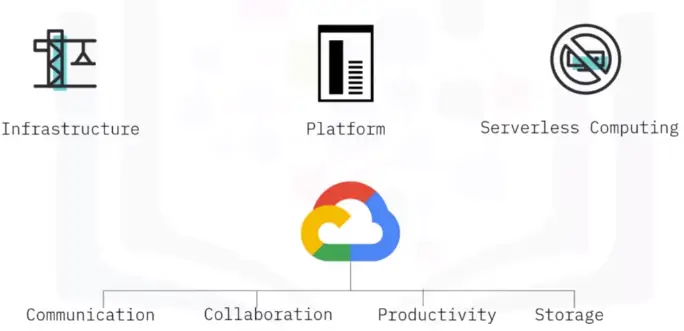
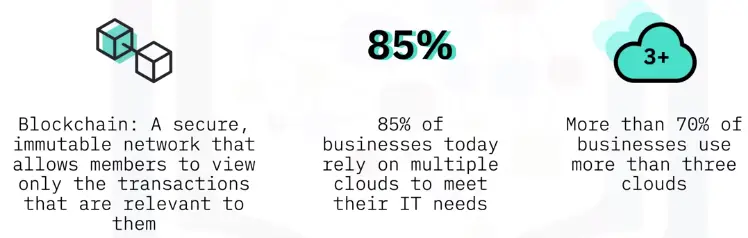
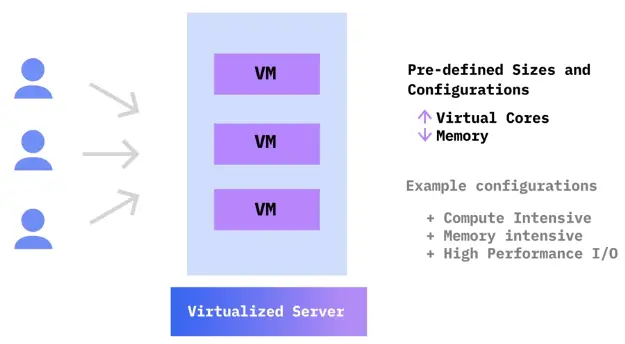
Cloud-based Storage Devices
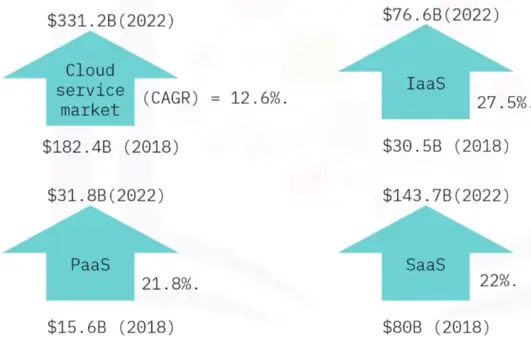
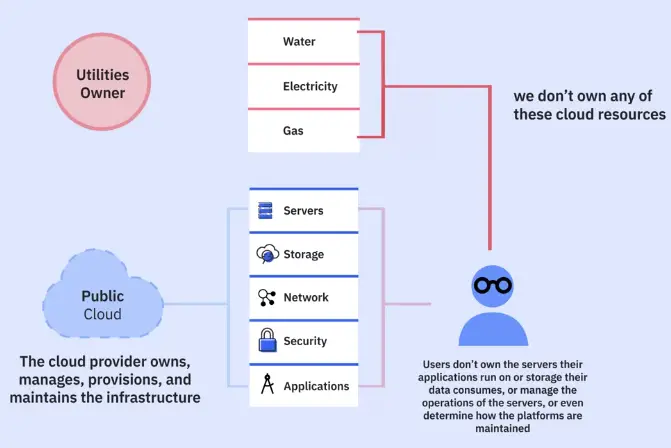
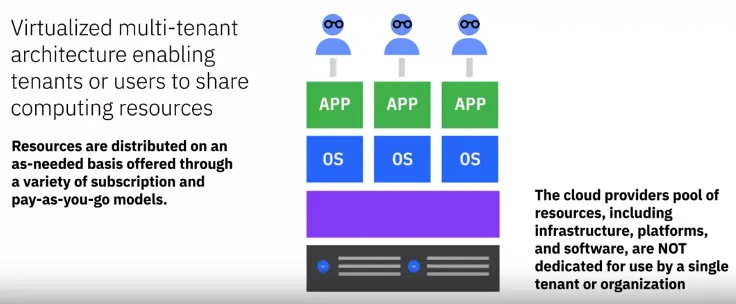
Cloud storage
Cloud storage is when files and applications are stored and engaged with via the Internet.
-
Cloud companies manage data centers around the world to keep applications functioning properly, and user data stored securely.
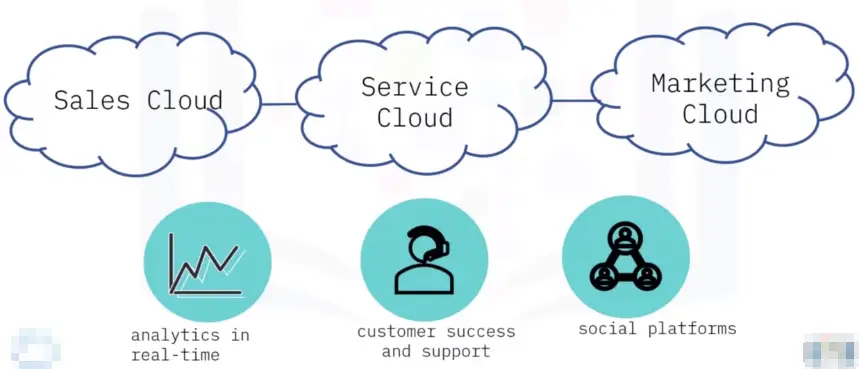
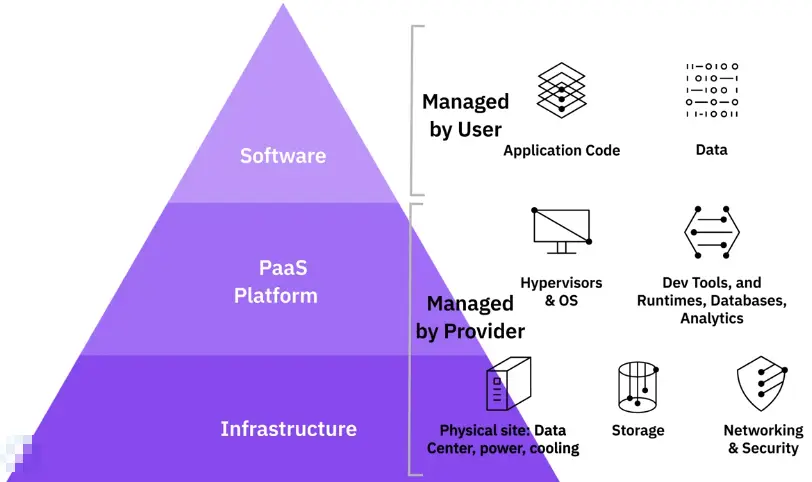
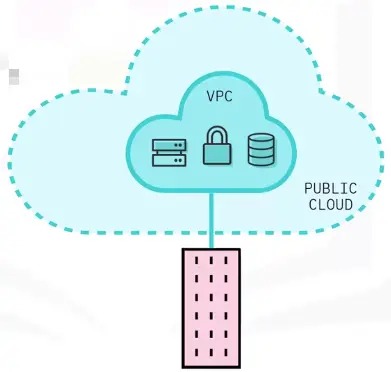
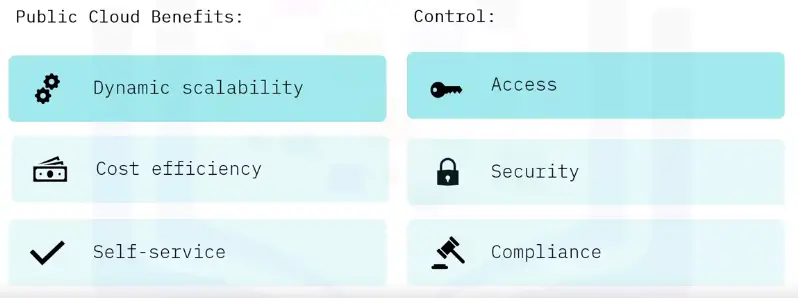
Public Cloud:
Provide offsite storage for Internet users.
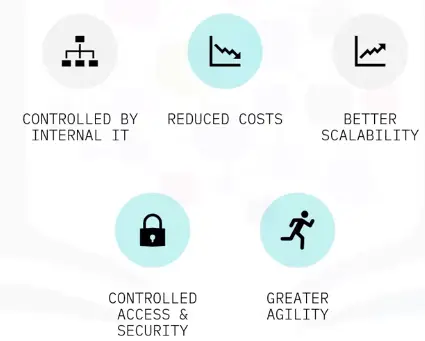
Private Cloud:
Provides collaboration and access to private network users.
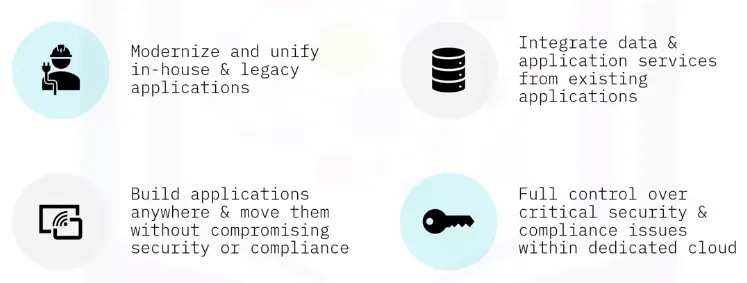
Hybrid Cloud:
A mix of both. Provides public sharing and restricted private areas via cloud storage and cloud-hosted apps.
File, Block, and Object storage
Cloud companies use multiple data storage types depending on how often they need to access different data and the volume of that data.
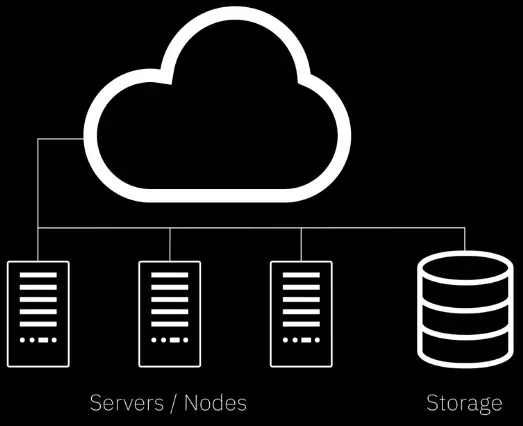
File Storage
File storage saves all data in a single file and is organized by a hierarchical path of folders and subfolders. File storage uses app extensions like .jpg or .doc or .mp3.
- Familiar and easy for most users
- User-level customization
- Expensive
- Hard to manage at larger scale
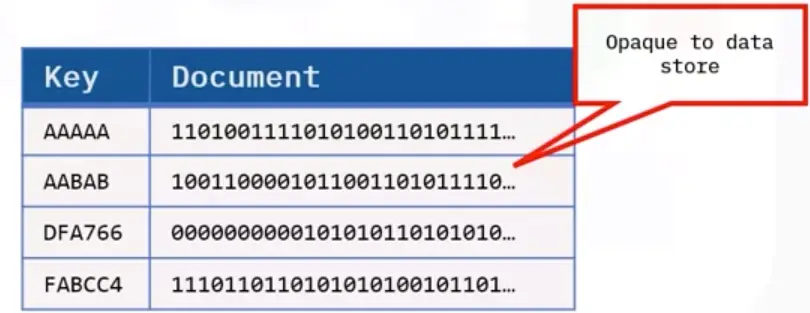
Block Storage
Block Storage splits data into fixed blocks and stores them with unique identifiers. Blocks can be stored in different environments (like one block on Windows, and the rest in Linux). When a block is retrieved, it’s reassembled with associated blocks to recreate the original data.
- Default storage for data that is frequently updated.
- Fast, reliable, easy to manage.
- No metadata, not searchable, expensive.
- Used in databases and email servers.
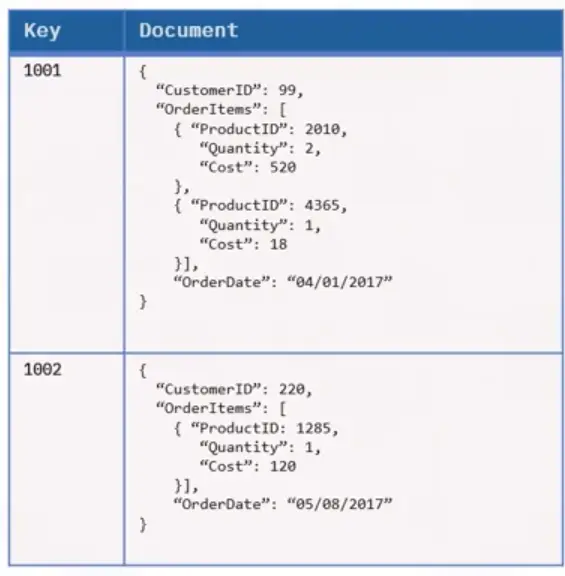
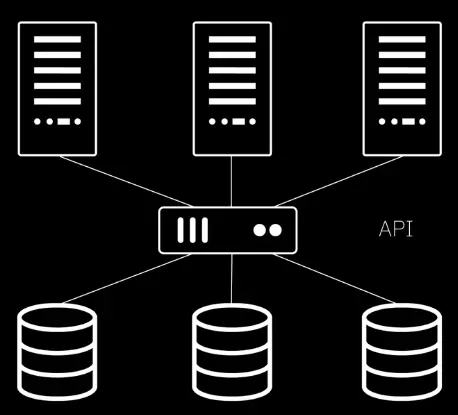
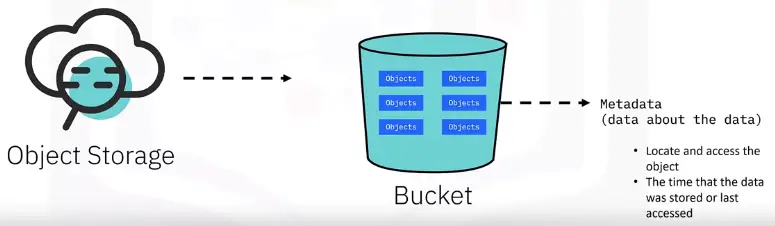
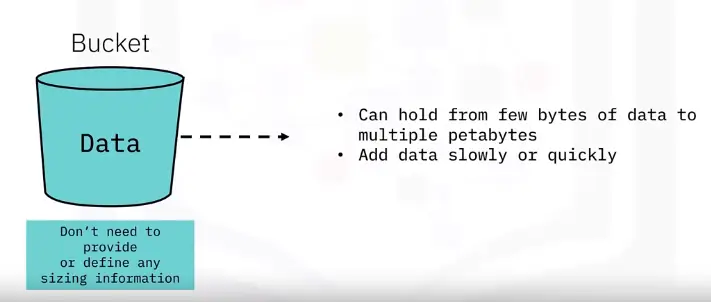
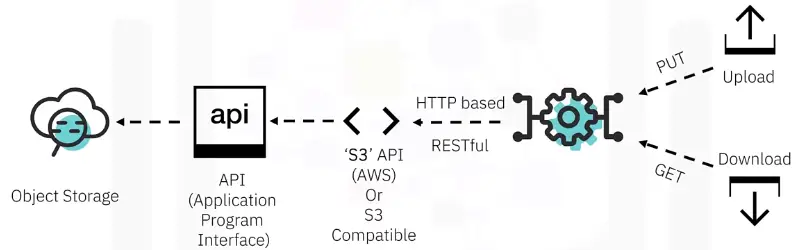
Object Storage
Object Storage divides data into self-contained units stored at the same level. There are no subdirectories like in file storage.
- Users metadata for fast searching.
- Each object has a unique number.
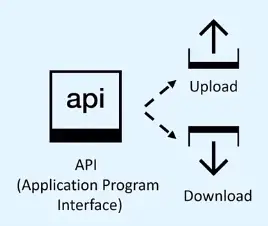
- Requires an API to access and manage objects.
- Good for large amounts of unstructured data.
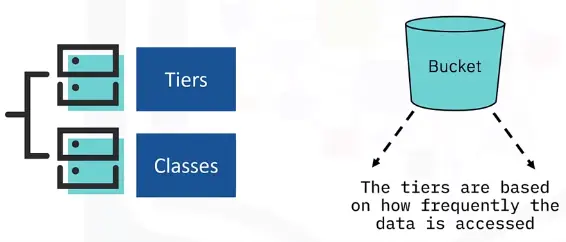
- Important for AI, machine learning, and big data analytics.
Storage gateways
A storage gateway is a service that connect on-premises devices with cloud storage.
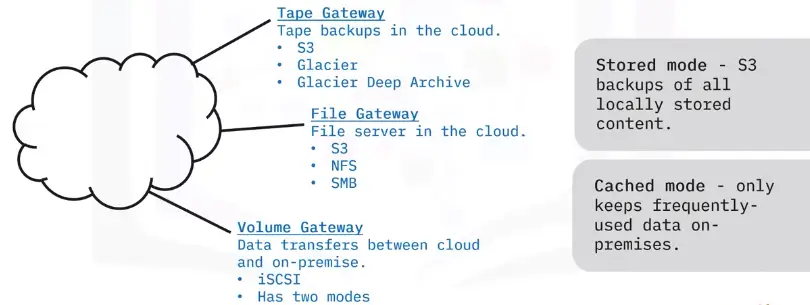

Archival storage


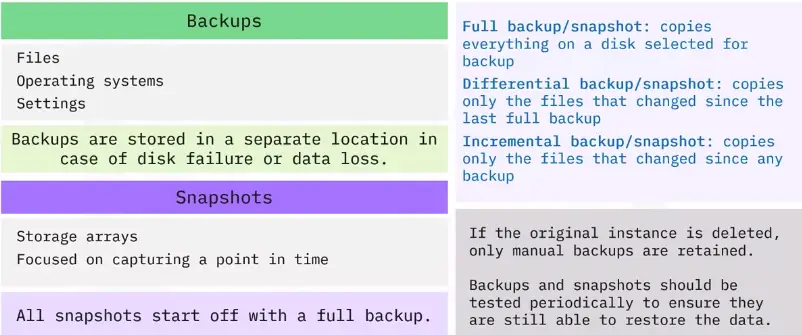
Backups and snapshots